Artificial intelligence is reshaping cybersecurity, not only for defenders but also for attackers. Every week, we read about new tools that make phishing campaigns more convincing, code generation faster, and social engineering more believable. The same algorithms that help us detect anomalies are now being used to create them. This is both fascinating and worrying.
In this article, we’ll explore how AI is changing attacker behavior and why the most effective defense lies in understanding what’s normal and spotting what’s not. You’ll also see how our team at Safetybits has translated that idea into a practical detection model for industrial environments, grounded in behavioral and stateful analysis and mapped to MITRE ATT&CK for ICS.
A few days ago, Google Cloud’s Threat Intelligence team published a report showing how threat actors are already leveraging AI to accelerate reconnaissance, exploitation, and automation in cyberattacks.
The conclusion is clear: AI doesn’t invent new attacks, it amplifies existing ones. But there’s one thing it can’t hide: behavior.
From IT to OT: the next frontier
AI assisted techniques are already common in IT environments, from deepfake phishing to automated vulnerability discovery. And if experience teaches us anything, what starts in IT eventually reaches OT.
Industrial networks are becoming more connected through remote maintenance tools, cloud linked gateways, and digital transformation projects. This connectivity brings efficiency but also exposure. It’s only a matter of time before AI augmented adversaries start applying the same level of automation and persistence to operational environments.
When that happens, traditional detection methods won’t be ready.
Why signature based detection falls short
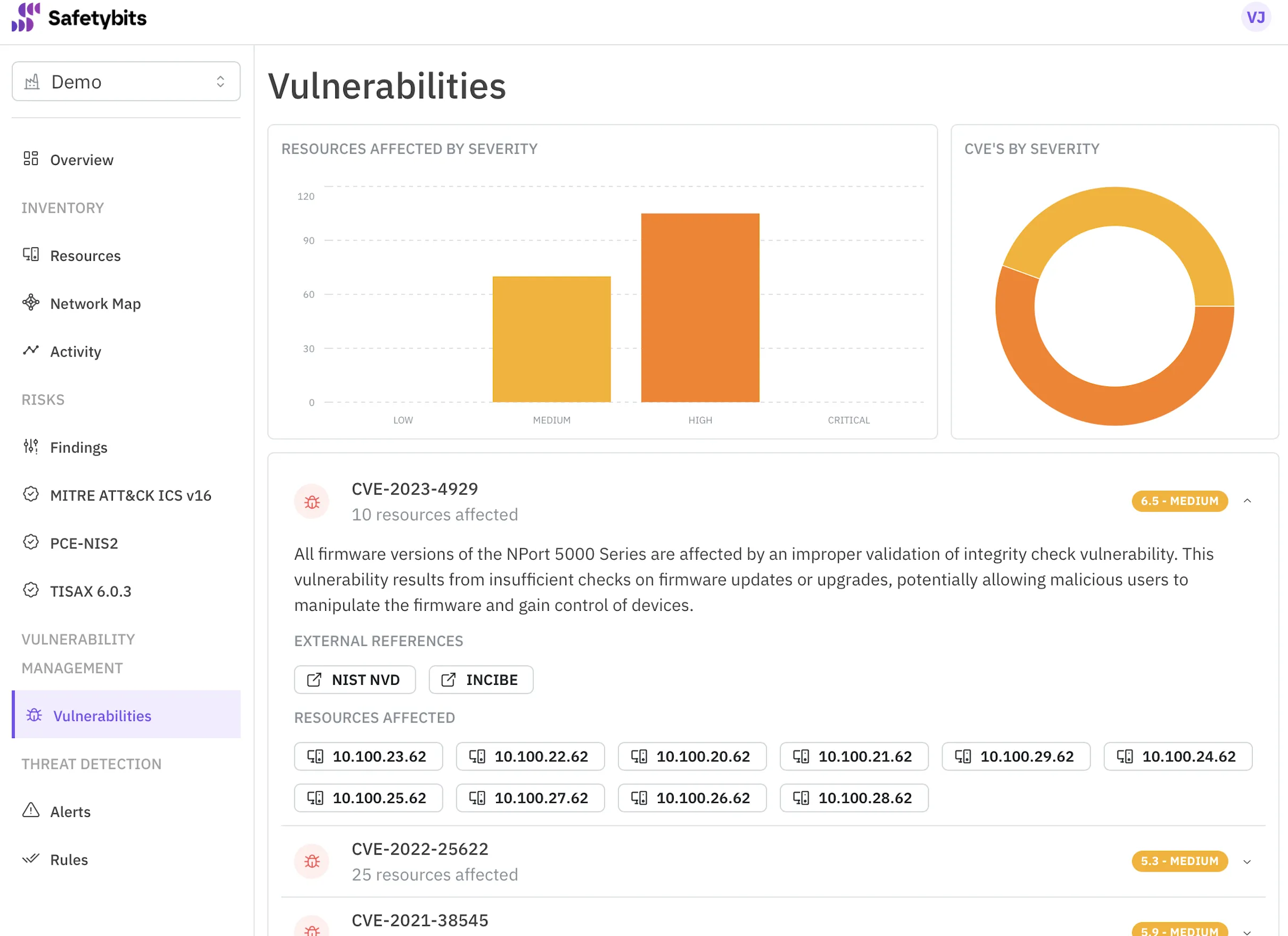
Most industrial cybersecurity solutions still rely on signatures and predefined attack patterns, a legacy of early intrusion detection systems. They recognize known threats but fail when confronted with something new, modified, or dynamically generated by an AI tool.
AI can create endless variations of payloads or commands faster than any threat feed can update.
In OT, where communication is deterministic and changes are rare, these variations can quietly bypass static defenses.
Signatures tell you what was known yesterday. Behavior tells you what’s happening now.
Detecting the abnormal: DPI, behavioral, and stateful analysis
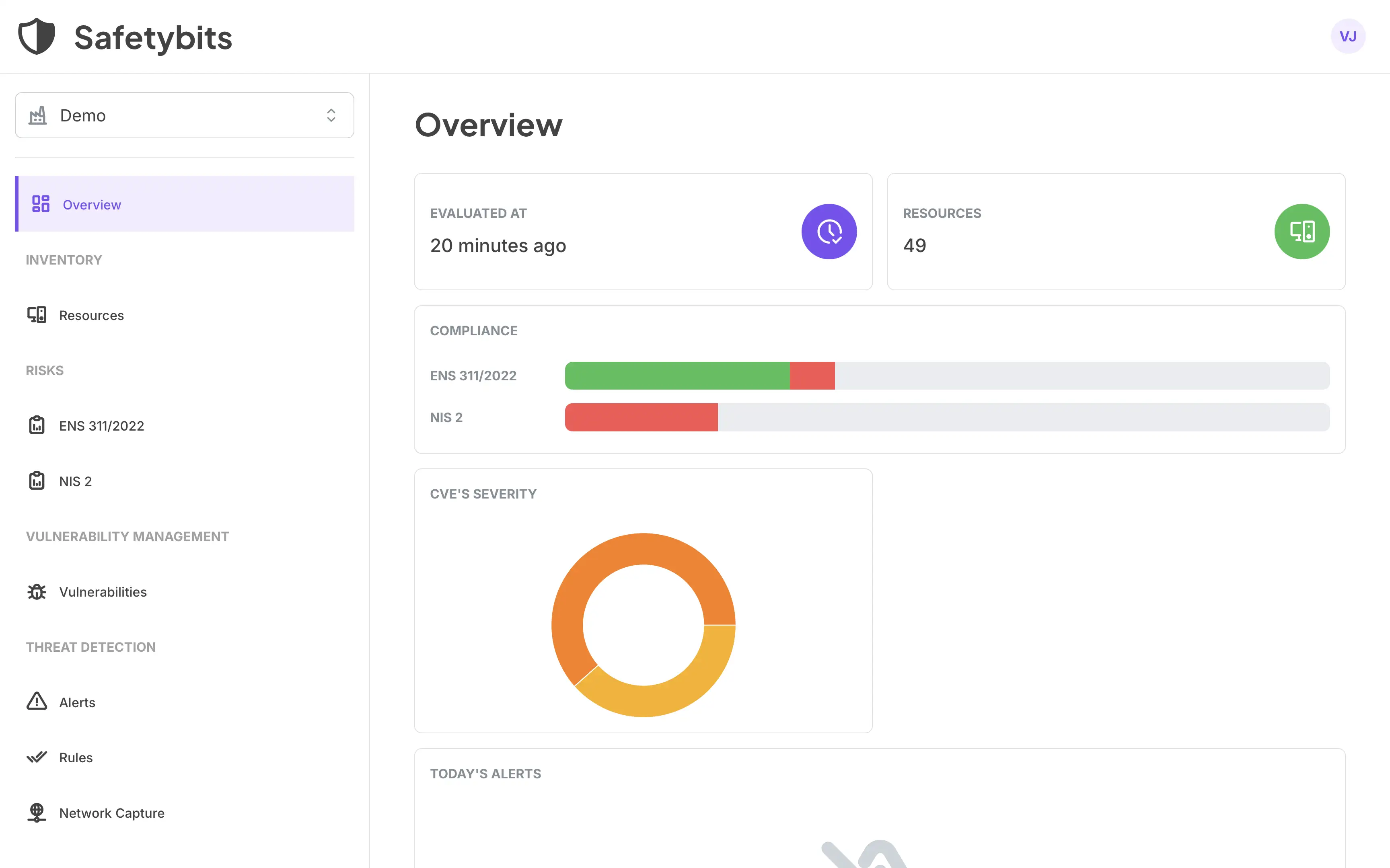
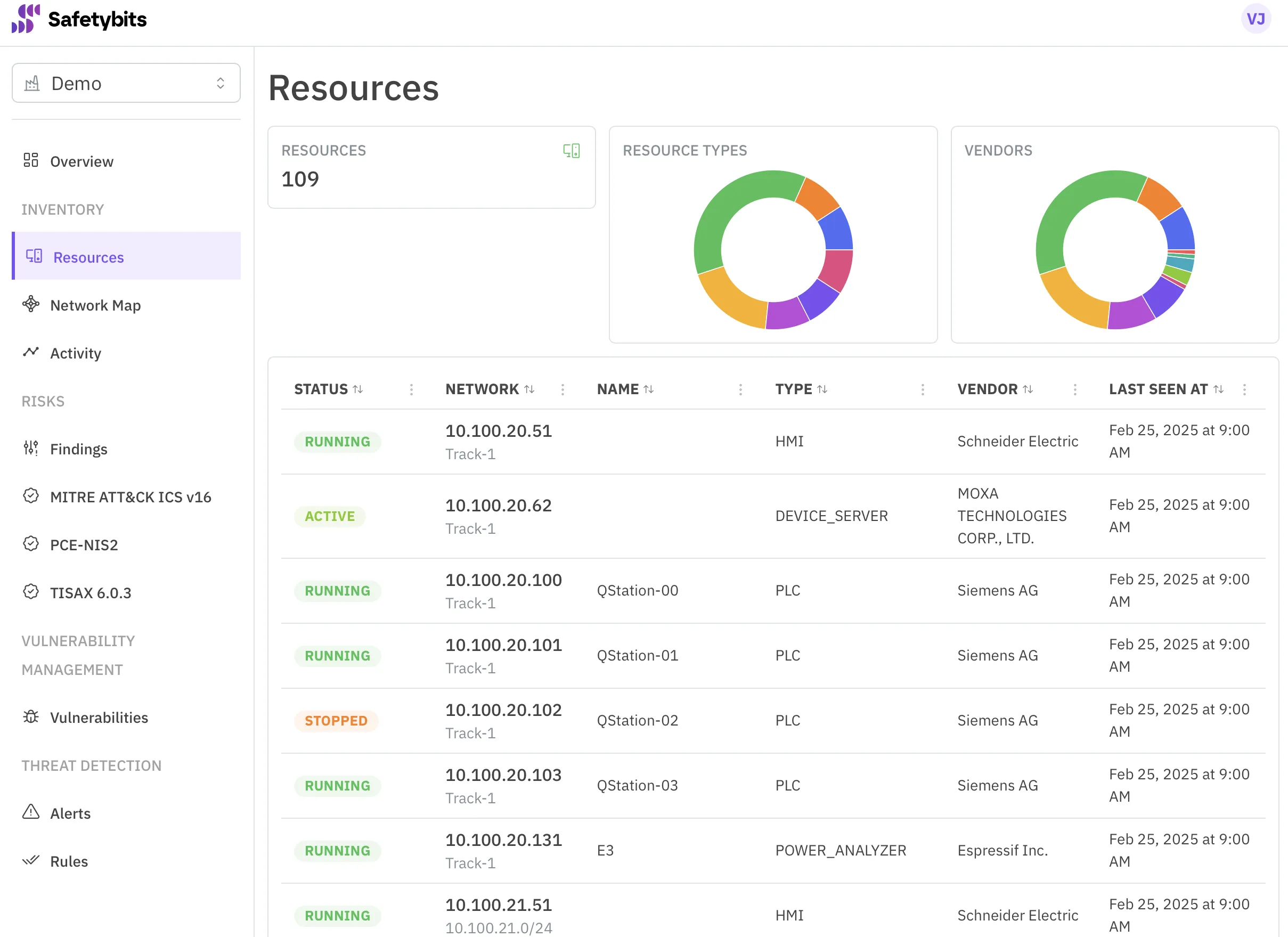
Behavioral anomaly detection for OT networks lies at the heart of AI powered threat detection. At Safetybits, we designed our detection engine with this principle in mind: understand what’s normal, and you’ll see everything that isn’t.
Our model combines three complementary capabilities:
- Deep Packet Inspection (DPI) parses industrial protocols such as S7, Modbus, OPC-UA, and DNP3, understanding the intent behind each command.
- Behavioral baselining learns the typical rhythm of communication between assets: timing, command sequences, maintenance windows.
- Stateful detection and machine learning correlate events over time, understanding transitions between operational states. This means we detect not just isolated anomalies but evolving behaviors that suggest automation or compromise.
With this hybrid model, anomalies become immediately visible:
- A PLC receiving write commands outside maintenance hours.
- An engineering workstation scanning unusual addresses or contacting new cloud endpoints.
- Subtle command sequence changes that indicate scripted activity instead of manual operation.
- Repeated behavioral shifts suggesting a progressive compromise rather than a single error.
Whether an attacker uses handcrafted scripts or AI generated exploits, their actions will deviate from the baseline, and stateful analysis ensures that context is preserved across events.
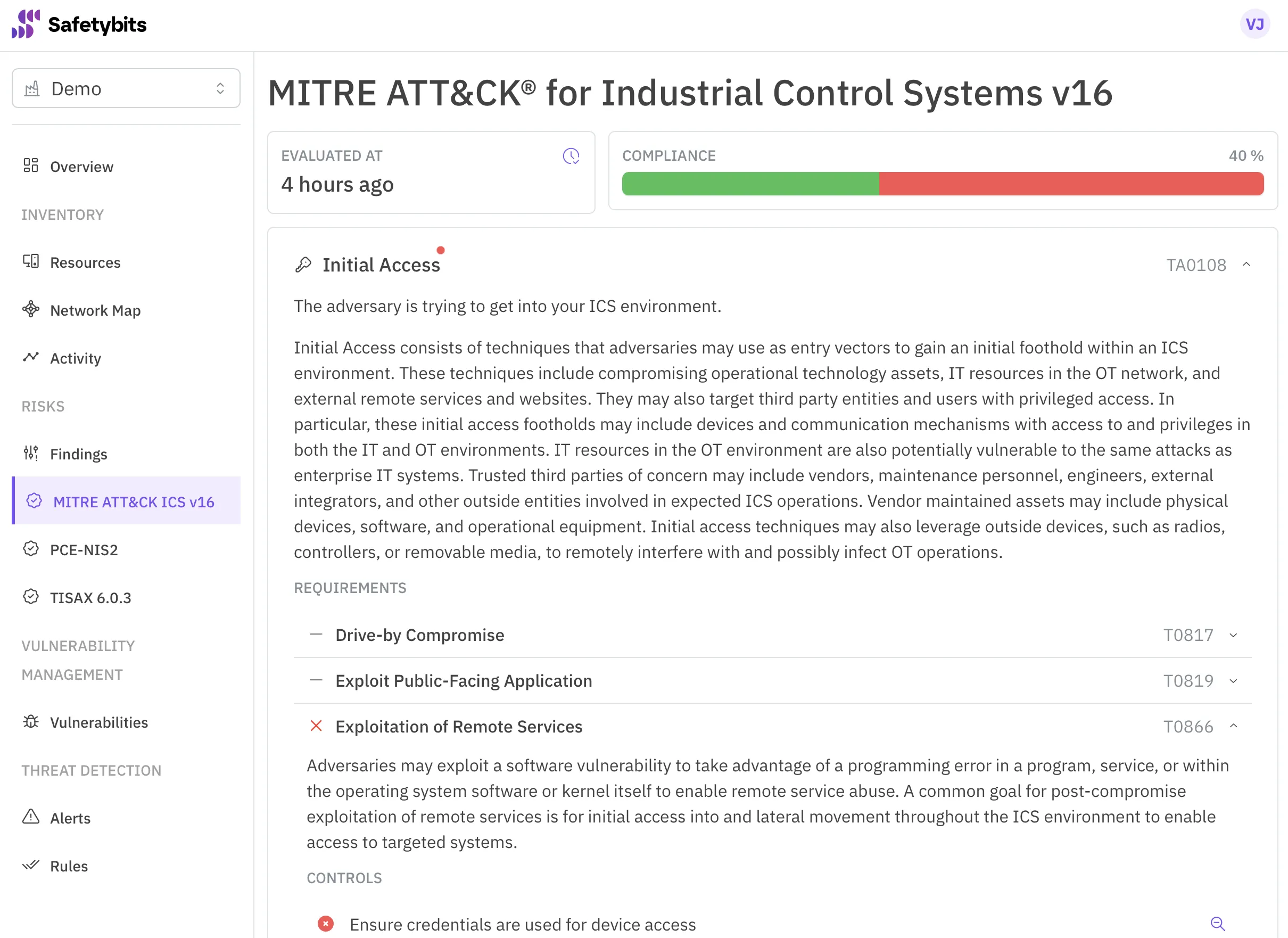
Mapping to MITRE ATT&CK for ICS
Mapping detections to MITRE ATT&CK for ICS transforms low level telemetry into a shared operational language. It allows analysts to classify alerts by adversarial intent, prioritize actions, and document incidents using a globally recognized framework.
| MITRE Tactic / Technique | Typical Behavior | Safetybits Detection |
|---|---|---|
| Remote System Discovery — T0846 (Discovery) | Enumeration of hosts and open ports, network sweeps, port scanning | DPI + flow analytics detect scanning patterns; behavioral baselines flag role deviations and new IPs contacting OT assets |
| Network Connection Enumeration — T0840 (Discovery) | Queries of active network connections, netstat like enumeration, unusual connection tables | Sensor level telemetry and state tracking surface unexpected connection enumerations and sudden role changes |
| Network Sniffing — T0842 (Discovery) | Passive capture or span port collection of network traffic to collect credentials or topology | Detect unusual promiscuous mode activities, mirrored traffic flows, or unexpected packet captures moving to external hosts |
| Automated Collection — T0802 (Collection) | Scripted or automated reads of PLC registers or OPC tags at scale | Behavioral baselines detect bursts of collection commands and abnormal polling frequencies |
| Data from Information Repositories — T0811 (Collection) | Bulk reads from engineering databases, schematics, or configuration stores | DPI reveals large or atypical file transfers or queries to known repository hosts; flow analytics detect sustained throughput |
| Exploitation of Remote Services — T0866 (Initial Access / Impact) | Exploiting vulnerabilities in remote facing services to gain code execution or access | Correlate new service behavior, anomalous sessions, and unusual command sequences with exploit indicators from DPI and stateful models |
| Standard Application Layer Protocol — T0869 (Command & Control / Lateral Movement) | Use of common protocols (HTTP, OPC, RDP, Modbus) for C2 or lateral traffic | Stateful detection links periodic beaconing, unusual use of application layer commands, and cross device command patterns |
This mapping bridges detections and operational response. It lets analysts translate alerts into attacker goals, automate response playbooks, and align findings with compliance frameworks.
MITRE ATT&CK defines the taxonomy. Safetybits delivers the signal.
Why this matters and how we differ
Traditional OT monitoring and IDS tools rely on static signatures and limited visibility. They spot what’s already documented but not what’s emerging.
At Safetybits, we built our detection engine for industrial environments where predictability is an advantage, not a constraint.
| Aspect | Traditional IDS | Safetybits Detection Engine |
|---|---|---|
| Detection logic | Signature & rule based | Behavioral + anomaly based |
| Visibility depth | Limited flow inspection | Full DPI for OT protocols |
| Learning model | Static, manual tuning | Adaptive baselining per device |
| Temporal context | Stateless, per event alerts | Stateful detections that understand sequences and device states |
| Response to unknown threats | Misses novel or AI generated activity | Detects deviation regardless of payload or tool |
| OT context | Generic IT/OT overlap | Purpose built for ICS (S7, Modbus, OPC-UA, DNP3 …) |
| Compliance integration | Optional mapping | Native correlation with MITRE ATT&CK for ICS, NIS2, and IEC 62443 |
Traditional IDS look for what they already know. Safetybits detects what shouldn’t happen.
The future of industrial detection
AI will change how attackers operate but not how they behave on the wire. To protect industrial networks, we need to shift from searching for known patterns to understanding the language of systems, their normal rhythm, relationships, and intent.
That’s the Safetybits philosophy:
- Learn the real behavior of your OT assets.
- Detect what’s abnormal in real time.
- Correlate context across time and devices to reveal hidden patterns.
- Respond before the anomaly becomes an incident.
Because even when attackers use AI, they still have to communicate, authenticate, and issue commands, and behavior exposes them.
Final thought
Coming from the cloud and container world, I learned early that you can’t hide abnormal behavior. Whether it’s a container spawning unexpected processes or a PLC suddenly changing its communication pattern, the principle is universal: visibility plus context wins.
AI changes the tools, not the behavior. And in cybersecurity, behavior is what betrays the attacker.
By combining Deep Packet Inspection, stateful detections and machine learning, and OT specific context, Safetybits detects what others can’t, providing clarity, context, and action for modern industrial defense.
Safetybits: detecting what’s abnormal, not just what’s known.
Expand your reach with OTSPM
The narrower your view, the less risks you can detect. Discover how an OTSPM platform leverages correlation to expand your reach.
Discover more →