Compliance is often seen as a hassle.
Implementing each security standard your company needs to comply with requires too much effort and provides limited benefits to daily operations.
Also, it’s not very effective at mitigating risks. You are secure at the moment you pass compliance checks, but what about five minutes later, a day later, or a week later? The longer it has been since the last check, the greater your chance of falling out of compliance without knowing it.
There is a visibility gap between checks. Most companies only run their compliance checks monthly, so it may be too late by the time they detect a risk.
The story completely changes when you implement continuous compliance, with multi-domain correlation with other security tools, in OTSPM style.
Implementing compliance has always been a pain point for us.
It required several man-hours to check every requirement of a security standard. And most of that work had to be repeated for each new standard we had to comply to.
With an OTSPM tool, our security controls were unified out-of-the-box and mapped to the appropriate requirement for each security regulation. This means we only have to tune each control once, and fixing one security risk is reflected in the progress across all the standards. With this, we reduced considerably our workload.
CIO, Leading automotive industry company
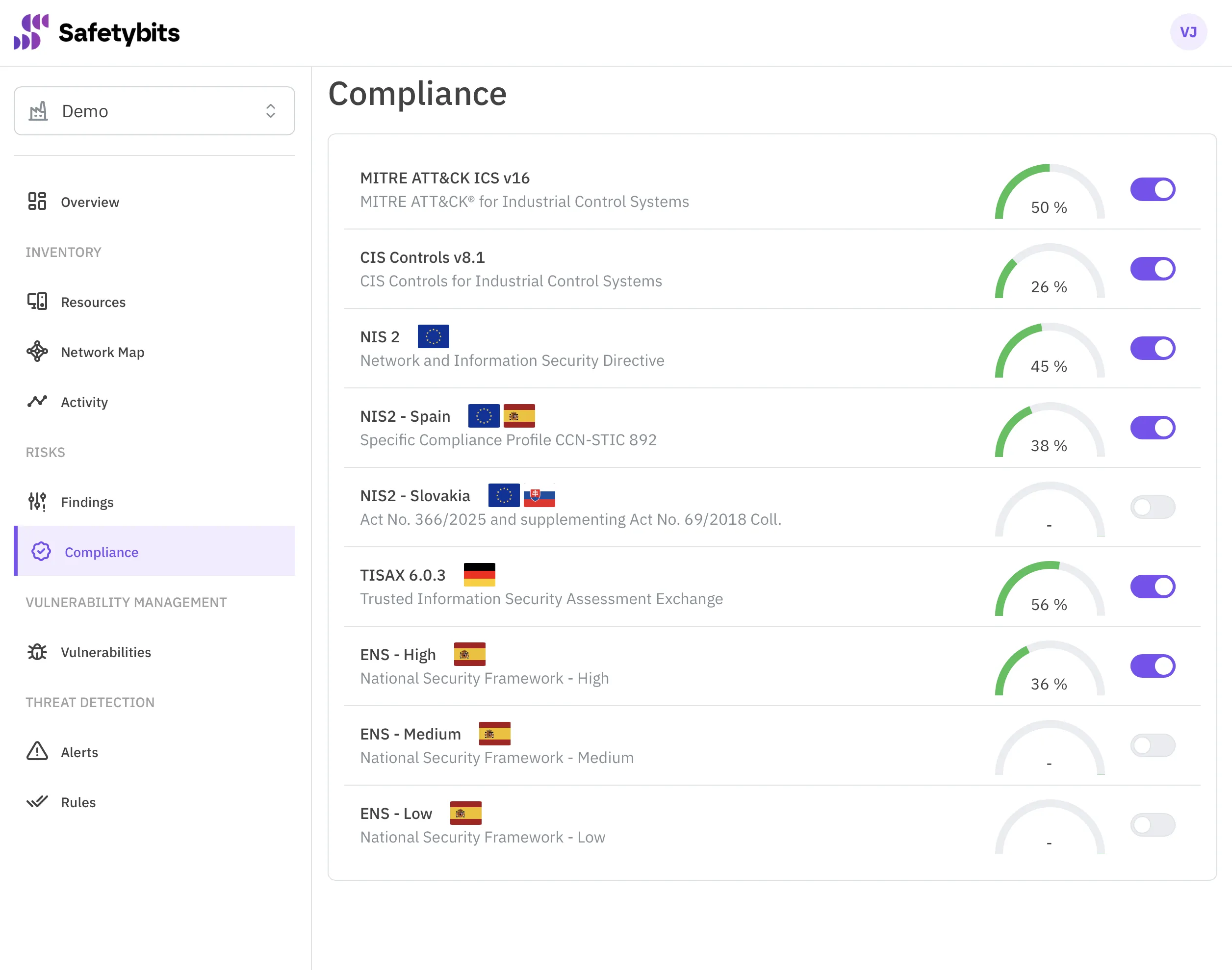
The Problem of Mapping Requirements to Controls
Security standards must cover many situations, so they are defined broadly. It’s up to you to adapt them to your specific infrastructure.
First, you need expertise to adapt each requirement adequately. Then, you need considerable effort to create the necessary controls for each requirement.
Although every security standard covers similar security best practices, each has a different focus and organizes requirements differently. As a result, effort is often duplicated when implementing controls for similar requirements in different security standards.
To make things worse, you won’t find out if you missed something until you fail an audit, which would mean that you have been at risk and may cause you to pay some fines or delay strategic business developments.
The Overwhelming Blank Page
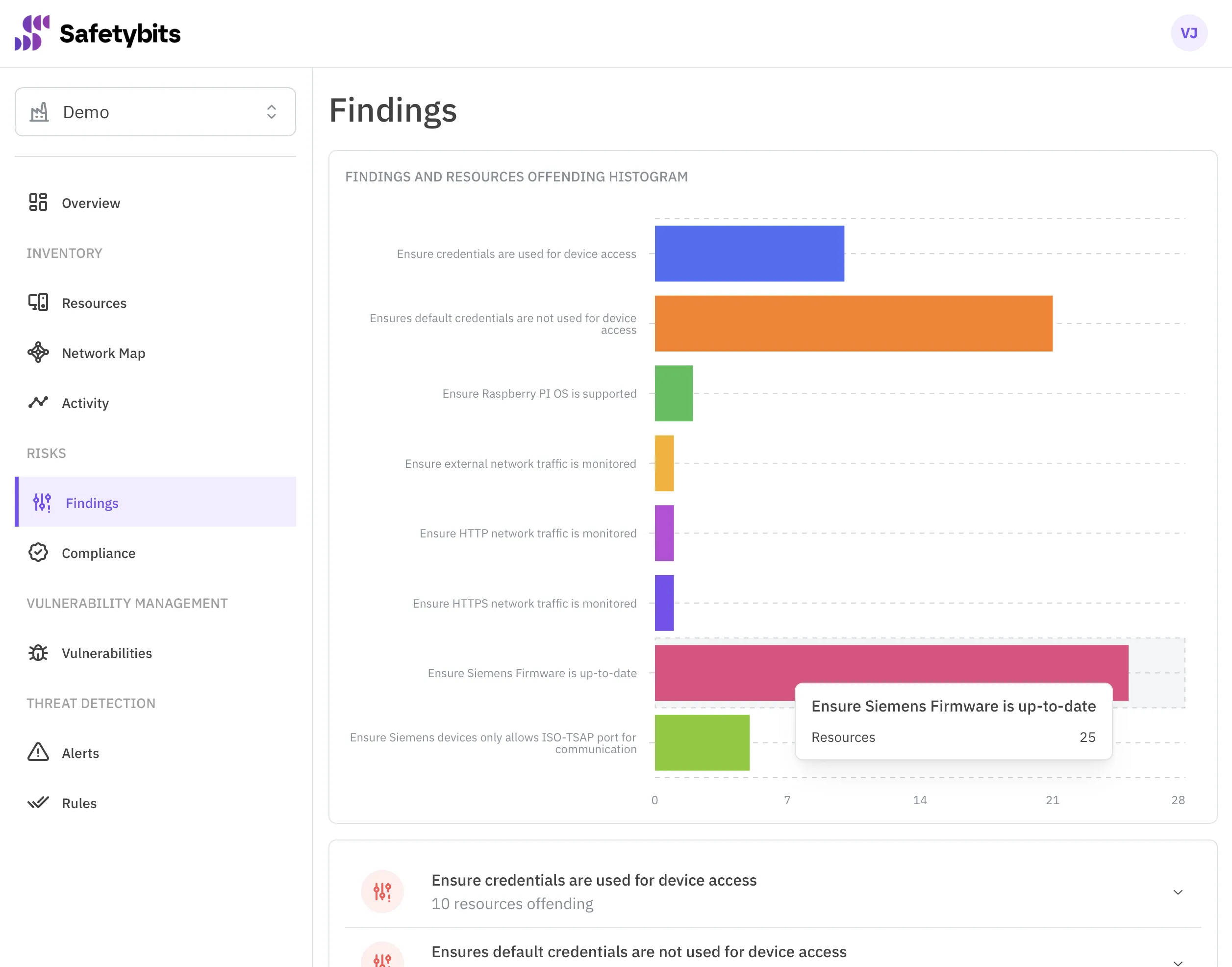
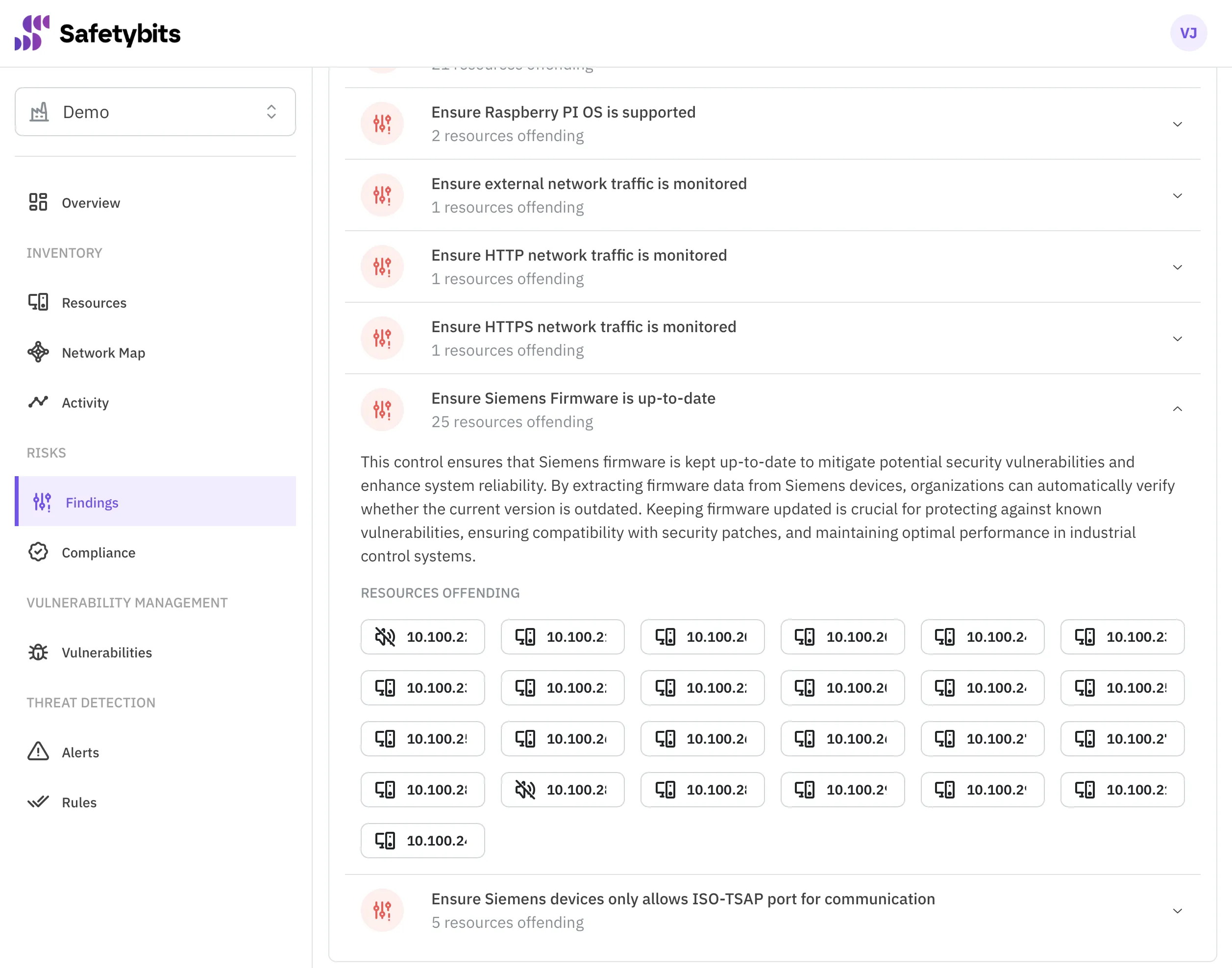
Once you implement all the controls, you suddenly face an overwhelming checklist of failing controls to fix. Where should you start?
You should start remediating the most critical risks, but you often lack the data to choose correctly.
Even if you are doing things right, you probably feel uneasy because you aren’t sure if you are doing it in the proper order or if you are missing something.
An Insight With Expiration Date
Finally, you pass all the compliance controls, giving you some sense of safety.
But you soon realize that checking security once every month is not enough. As time passes, it becomes more probable that a new risk will appear or something will get misconfigured, and you may not detect them until it’s too late. That’s why we say that a compliance check rots over time.
Automating the controls in a way that can be run more often requires too much effort, so most teams don’t invest more in compliance and implement other security measures instead.
Without value for daily operations, compliance ends up being an annoying checklist you are required to fill out from time to time.
How the OTSPM Approach Changes the Game
That’s how the story has been up until now, but things don’t have to be this way, and a new approach to security is becoming increasingly popular.
Security solutions that follow the OTSPM principles have a completely different approach to compliance. These principles are:
- OT is not IT: Use specialized tools to cover the gaps that regular security tools have in OT.
- Security is continuous: Everything should be automated by default to get an up-to-date picture.
- Security is a whole: By deeply integrating security tools with each other, you obtain context that helps you make decisions.
Let’s see how these three simple practices change the game completely.
Out-of-the-Box Controls
To effectively map security requirements to compliance controls, you need security expertise, deep knowledge of your infrastructure, and multi-domain data correlation (across inventory, vulnerability management, and threat detection).
OTSPM solutions have it all:
- Integration with OT equipment to gather relevant data.
- Engines that correlate data from several sources and can see the whole picture.
- They are created by experts who study security standards and regulations.
For example, through the inventory, they know the firmware version of your devices and can warn you when they are outdated.
Similarly, threat detection knows if you have enabled a detection rule to detect a specific threat.
That’s why OTSPM solutions can provide automated out-of-the-box controls that cover everything related to OT and allow you to start securing your infrastructure immediately.
Unified Controls
While you will need to tune some points specific to your setup, you’ll begin with almost all the work done, and the tuning process will be easy.
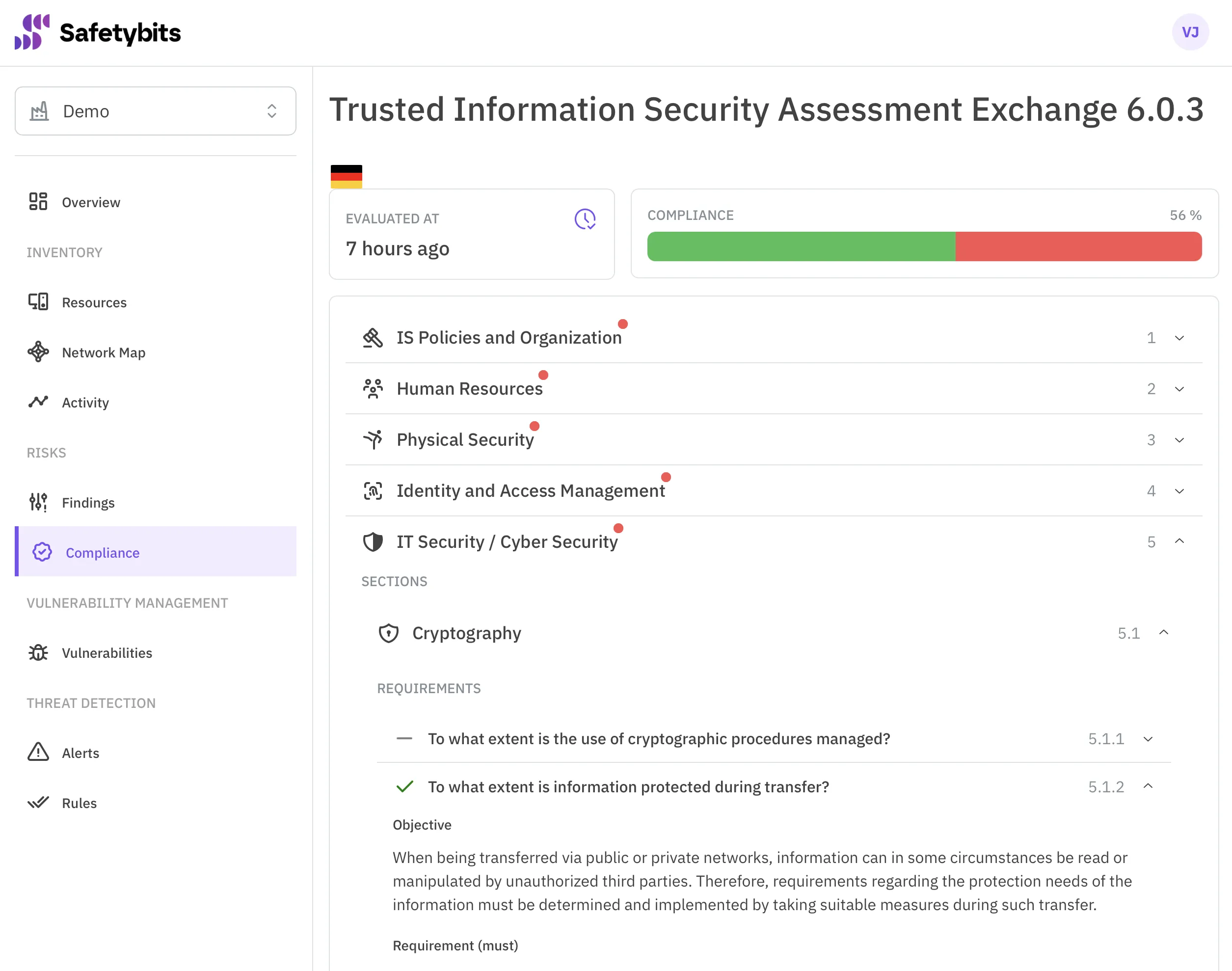
OTSPM solutions tend to map each compliance requirement to one or many automated controls that are reused all around. That means you’ll only need to tweak a control once, and the effect will apply to the compliance score of every security standard.
Prioritize What’s Critical
The severity of a specific risk and the number of devices susceptible to it can be calculated by correlating data from inventory, vulnerability management, and threat detection.
As we’ve said, OTSPM solutions have this data and will prioritize your risks. This allows you to plan your actions to have a more significant impact.
My team really engaged in improving our compliance score thanks to the prioritization. Having clear guidance on what is more critical and how to remediate the risks, helped us see the impact of our work and motivated us to fix all the issues in record time. It felt almost like a video game.
Maintenance Manager, Automotive components company
Controls That are Checked Continuously
As those out-of-the-box controls are fully automated, OTSPM solutions can run them several times daily. Frequent checks reduce the visibility gap and allow you to act as soon as something falls out of compliance or a new risk is detected.
Compliance hasn’t been fully useful for us but rather a chore, by the time we realized something was out of compliance we had been at risk for too long.
Adopting OTSPM has completely changed the game. Our security posture is always up-to-date so our security team can act as soon as something falls out of compliance.
Compliance is now a core practice in our security strategy, we feel more confident overall, and security audits are a bit less scary.
CISO, Leading automotive industry company
Conclusion
Compliance has always been a core security area, helping companies identify and remediate risks.
However, the lack of proper tools has turned compliance into a black sheep.
An OTSPM approach completely changes the game, increasing compliance value and reducing its implementation cost by several orders of magnitude.
Seamless Compliance
Safetybits Seamless Compliance continuously checks your security requirements and guides you through mitigation actions.
Discover more →