The European NIS2 directive arrived in 2024 to Europe to set a new high bar on the union’s cybersecurity.
So far, the directive defines only a set of guidelines that state members were expected to transpose into local laws by October 17. However, it’s been a few months, and only a few countries have done their homework. Luckily, this is enough to let us know what to expect from the implementation of this directive.
In this article, we’ll cover how it affects industrial environments with what we know so far.
ℹ️ Note
2025-06-09: We’ve updated this article with new information on the NIS2 directive for Denmark, Estonia, Finland, and Lithuania.
2025-01-21: We’ve updated this article with new information on the NIS2 directive.
Why is NIS2 Needed?
In recent years, we’ve seen increasing adoption of technologies in every aspect of our lives. What used to be isolated is now connected, and we complement our personal computers with smartphones, smartwatches, smart TVs, and other smart devices.
Attackers have adapted to this new landscape. Cyberattacks rose by 57% in 2023, and the trend continued in 2024.
And more importantly, we’ve seen examples of attacks targeting essential infrastructure in the last years:
- Santa Barbara Systems (2024).
- Orange Spain (2024).
- Santander Bank (2024).
- Barcelona’s Hospital Clinic (2023).
- Royal Mail (2023).
- ABB (2023).
- Ukraine Electric Power Attack (2022).
Also, the relationship between cyberattacks and warfare is clearer than ever, given the current geopolitical situation in Europe.
With this in mind, the NIS2 directive aims to increase Europe’s cyber resilience and protect its essential services.
Status of the Transposition on State Members
These are, so far, the countries that have adopted the NIS2 directive into their local laws.
| Country | Status | Observations |
|---|---|---|
| 🇦🇹 Austria | ⚠️ Ongoing | |
| 🇧🇪 Belgium | ✅ Enacted | |
| 🇧🇬 Bulgaria | ⚠️ Ongoing | |
| 🇭🇷 Croatia | ✅ Enacted | |
| 🇨🇾 Cyprus | ⚠️ Ongoing | |
| 🇨🇿 Czech Republic | ⚠️ Ongoing | |
| 🇩🇰 Denmark | ⚠️ Ongoing | Enacted. Sector-specific laws expected for July 2025. |
| 🇪🇪 Estonia | ⚠️ Ongoing | |
| 🇫🇮 Finland | ✅ Enacted | |
| 🇫🇷 France | ⚠️ Ongoing | |
| 🇩🇪 Germany | ⚠️ Ongoing | |
| 🇬🇷 Greece | ✅ Enacted | |
| 🇭🇺 Hungary | ✅ Enacted | |
| 🇮🇪 Ireland | ⚠️ Ongoing | |
| 🇮🇹 Italy | ✅ Enacted | |
| 🇱🇻 Latvia | ✅ Enacted | |
| 🇱🇹 Lithuania | ✅ Enacted | |
| 🇱🇺 Luxembourg | ⚠️ Ongoing | |
| 🇲🇹 Malta | ⚠️ Ongoing | |
| 🇳🇱 The Netherlands | ⚠️ Ongoing | |
| 🇵🇱 Poland | ⚠️ Ongoing | |
| 🇵🇹 Portugal | ⚠️ Ongoing | |
| 🇷🇴 Romania | ✅ Enacted | |
| 🇸🇰 Slovakia | ✅ Enacted | |
| 🇸🇮 Slovenia | ⚠️ Ongoing | |
| 🇪🇸 Spain | ⚠️ Ongoging | It will be based on ENS. |
| 🇸🇪 Sweden | ⚠️ Ongoing |
After examining the already enacted laws and the available drafts, it’s clear that countries are adapting existing regulations rather than reinventing the wheel.
That’s good news! Even if the NIS2 directive hasn’t been transposed in your country, you can prepare by implementing security best practices. The drafts are based on that, and the final regulation won’t deviate much from them.
⚠️ Warning
Don’t wait too long to start preparing. Almost every state member that hasn’t enacted a transposition has a bill in discussion that may be signed into law at anytime.
What Does the NIS2 Directive Look Like?
It won’t come as a surprise, but the directive is a rather boring document that spans 60 pages and is divided into 46 articles.
Most articles describe the new European security network and the framework the Member States need to implement. The requirements affecting businesses are mainly described in articles 21 and 23.
| Section . | Topic |
|---|---|
| Chapter 1 Articles 1-6 | General provisions: Covers the scope of the directive and defines common terms. |
| Chapter 2 Articles 7-13 | Coordinated cybersecurity frameworks: Lists the new entities each Member State needs to define. |
| Chapter 3 Articles 14-19 | Coordination at union and international level: Defines the new entities that will be needed at an European level. |
| Chapter 4 Articles 20-25 | Cybersecurity risk-management measures and reporting obligations: ⚠️ Provides a framework on what measures organizations will need to implement. Also covers how reporting of incidents will take place, and the communication flow between all entities. |
| Chapter 5 Articles 26-28 | Jurisdiction and registration: Defines who is the authority each entity will respond to. Also adds some requirements for DNS providers, TLD registries and other hosting companies. |
| Chapter 6 Articles 29-30 | Information sharing: Covers how Member States will communicate and coordinate to flag threats and raise security awareness. |
| Chapter 7 Articles 31-37 | Supervision and enforcement: ⚠️ Lists how Member States will be able to audit the measures taken by entities and enforce proper implementation. Here, on article 34 is where the fines are defined. |
| Chapters 8 & 9 Articles 38-46 | Delegated and implementing acts, and Final provisions. |
As you may have noticed, the security requirements are just a tiny portion of the directive. A big chunk of it is dedicated to creating a dense network of entities that work together to monitor security incidents, supervise the implementation of security measures, and coordinate efforts to adapt to new threats.
This network can be split into three blocks. Here is a summary description; please refer to the complete directive for the full context.

Every Member State must:
- Transpose the directive into local laws by October 17th (2024), defining the specific requirements entities must comply with.
- Define the competent authorities that will supervise and enforce the directive.
- Define the CSIRTs (Computer Security Incident Response Teams) coordinating the vulnerability disclosures. Competent authorities can form them.
- Name a single point of contact.
The EU CyCLONe Cooperation Group has been created:
- Formed by representatives of Member States, the commission, and the European Union Agency for Cybersecurity (ENISA).
- With the intervention of the European Supervisory Authorities (ESAs), the competent authorities, the European Parliament, and representatives of relevant stakeholders.
A CSIRTs Network has also been created:
- To promote cooperation among Member States by exchanging information, ensuring interoperability, implementing coordinated responses…
- It’s composed of representatives of the CSIRTs, the Commission as an observer, and is assisted by ENISA.
Who is Affected by NIS2?
The following entities are affected by the NIS2 directive and must implement security requirements.
Medium and Big companies in the following segments.
High criticality segments:
- ⚡️ Energy: Electricity, district heating and cooling, oil, gas, hydrogen.
- 🚅 Transport: Air, rail, water, road.
- 🏦 Banking.
- 📈 Financial market infrastructures.
- 🏥 Health.
- 💧 Drinking water.
- 🚱 Wastewater.
- 💻 Digital infrastructure.
- 💁🏼 ICT service management (b2b).
- 🏢 Public administration.
- 🚀 Space.
Other critical sectors:
- 📨 Postal and courier services.
- 🚮 Waste management.
- 🧪 Manufacture, production, and distribution of chemicals.
- 🥘 Production, processing, and distribution of food.
- 🏭 Manufacturing: Medical and in vitro diagnostic devices, computer electronic and optical products, electrical equipment, machinery and equipment, motor vehicles trailers and semi-trailers, and other transport equipment.
- 💻 Digital providers.
- 👩🏽🔬 Research.
Companies on given segments independent of size:
- Providers of electronic communications networks and services.
- Trust service providers and domain name registries.
- Any company that is essential in any way:
- If they are the sole provider in a Member State of an essential service.
- If a disruption of the service could induce a significant systemic risk.
- The entity is a public administration entity.
These entities are also classified by their importance.
Essential entities are those in the “high criticality segments” and the “companies independent of size”.
The rest are classified as Important entities.
This is a summarized description. Please refer to the full directive to obtain the complete context.
NIS2 Fines
The NIS2 doesn’t provide much detail into what fines can be expected. It just defines two maximums and leaves the Member States to provide more detail.
Essential entities: administrative fines of a maximum of 10.000.000 €, or 2 % of the total worldwide annual turnover, whichever is higher.
Important entities: administrative fines of a maximum of 7.000.00 €, or 1,4 % of the total worldwide annual turnover, whichever is higher.
This doesn’t mean you’ll get fined that much on top of suffering a cyberattack. The directive positions itself as an understanding companion, taking into account your circumstances.
ou should be ok as long as you demonstrate good faith by implementing the security requirements and notifying any incident as soon as you are aware of it.
Direct Impact on the Affected Industries
Now that we understand the full scope of the NIS2 directive, let’s get to the meat of it. What does this mean for your business?
At the top executive level
One of the biggest changes of NIS2 is that now the management level of a company must be involved in the cybersecurity measures taken.
This symbolizes the paradigm shift the directive is pushing for: From now on, cybersecurity must be at the core of any entity, and the top must lead the change.
IT / OT departments
There aren’t big changes for any IT / OT department that already implemented cybersecurity. The requirements from NIS2 are basic or medium cybersecurity best practices.
However, those industries at the beginning of their cybersecurity journey will need to put in some effort.
The requirements to implement are:
- Policies on risk analysis and IT security.
- Incident handling.
- Business continuity (backup and disaster recovery, crisis management).
- Security in network and IT system acquisition, development, and maintenance. Including vulnerability handling and disclosure.
- Policies and procedures to assess the effectiveness of cybersecurity risk-management measures.
- Basic cyber hygiene practices and cybersecurity training.
- Policies and procedures regarding the use of cryptography and, where appropriate, encryption.
- Human resources security, access control policies, and asset management.
- The use of multi-factor authentication or continuous authentication solutions, secured voice, video, and text communications, and secured emergency communication systems within the entity, where appropriate.
- Application of coordinated security risk assessment.
The main concern right now is how the Member States will adapt these guidelines into concrete requirements. Will they opt for an easy-to-comply regulation or stand up to the challenge and build comprehensive regulation? We’ll hopefully know on October 17th.
Supply Chain
One of the new aspects of NIS2 is securing the supply chain regarding technology providers.
This is securing the relationship between yourself and anyone who provides you with services like hardware, cloud services, internet domains, email services…
The supply chain has been a major target for attackers. Regarding industry, one of the main attack vectors is identity theft via email. For example, an attacker may gain access to an email account, gather information for a while, then impersonate one of your providers and send invoices to be paid (to their bank account).
Another growing attack vector is vulnerabilities in hardware devices. More and more devices in a production plant need a network connection. However, not all providers implement security best practices.
The directive’s heart is in a good place, but this part has quite a broad description. Let’s hope local laws scope properly this aspect of NIS2.
Reporting
The star of NIS2 is reporting security incidents. We mentioned earlier that one of the motivators for fines is not reporting a security incident on time.
The directive puts the focus on coordinating several local entities to see the big picture and being proactive in assisting by detecting threats. But to reach that goal, you need an “early warning system" driven by organizations reporting every security incident as it’s discovered.
Entities must report significant incidents to the competent authority, who will forward them to the CSIRT. An incident is considered as significant if it caused or is capable of causing either severe operational disruption or financial loss; or if it affects natural or legal persons by causing material or non-material damage.
The timing will also be important:
- Incidents must be reported within 24 hours of becoming aware. On this initial report, you should include suspicions of the incident being unlawful, malicious, or having a cross-border impact.
- You must update within 72 hours with an initial assessment including the severity of the incident, the impact, and indicators of compromise.
- You may also need to report with relevant status updates if requested by the CSIRT or competent authority.
- A final report will be needed within 1 month with a detailed description of the incident, the type of threat or root cause, the mitigation measures taken, and the cross-border impact.
Reporting is rather concrete in the NIS2 directive. We are only waiting for local authorities to define the actual format and communication method of the reports.
Inspections
Finally, the directive takes into account inspections and audits, as no norm is worth its weight in gold unless it’s properly enforced.
Competent authorities can perform on-site inspections and targeted security audits and may request any information and evidence of the implementation of cybersecurity policies.
Conclusion
The European NIS2 directive is a needed regulation to ensure the safety of essential resources in Europe.
Its scope is ambitious, expanding from just security requirements to building a whole network of entities that will safeguard strategic organizations.
However, the European Union’s federated nature makes implementation slightly more challenging. The Member States now need to finish adapting the directive to local laws, and we won’t know the concrete details of the regulation until they do.
This uncertainty is far from desirable, moreover when such high fines are on the table, but keep in mind the understanding companion nature of the directive. If you are worried about it, start implementing cybersecurity best practices, you’ll both demonstrate good faith and be protected.
Speed up Your Flow
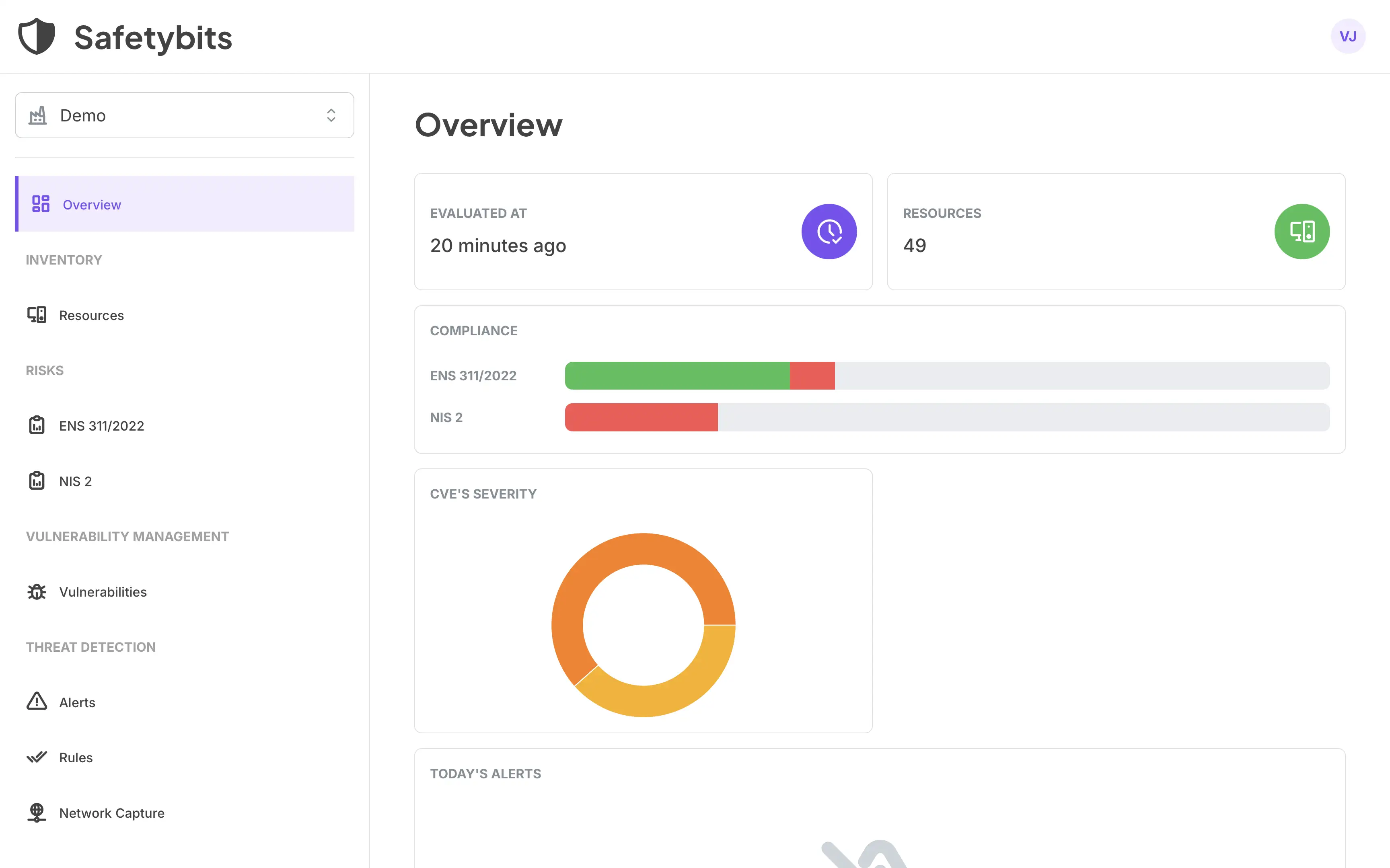
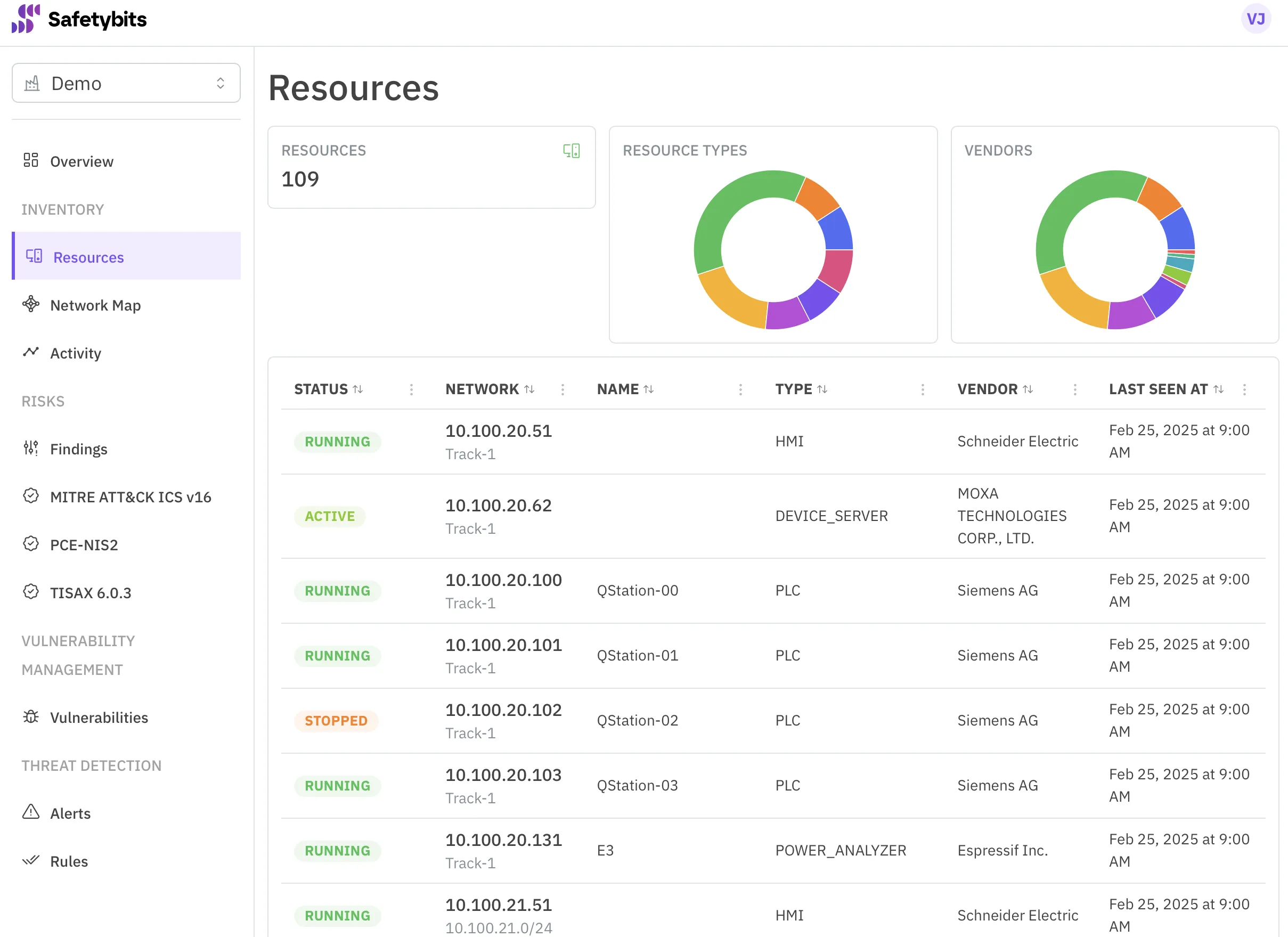
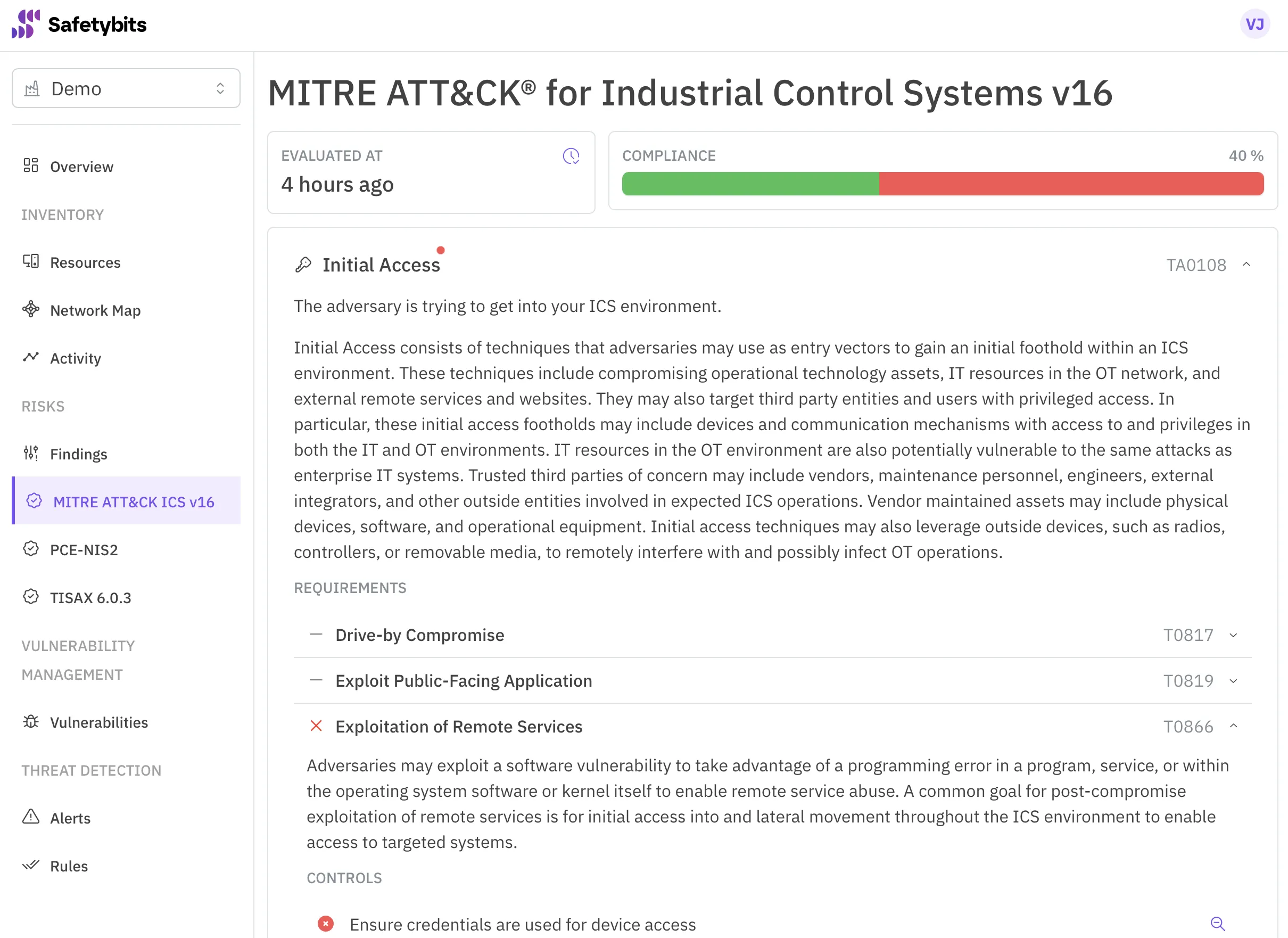
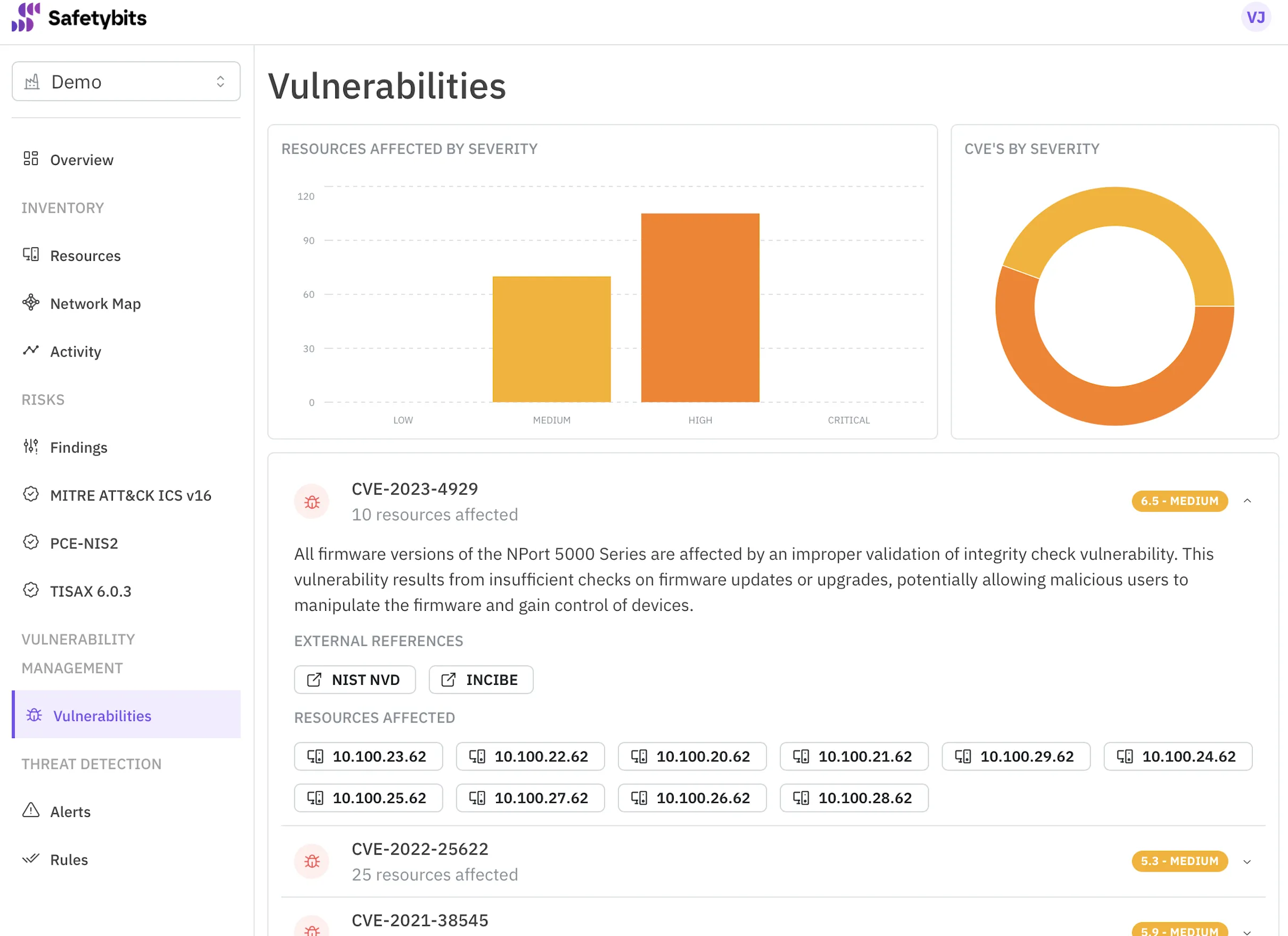
Safetybits OTSMP Platform automatizes tasks and gives you insights so you can jump straight to the action.
Discover more →