Safetybits introduces Continuous Inventory to uncover all hidden devices in your infrastructure, providing an accurate picture over time. It gathers device metadata from multiple brands, enriching real-time findings and suggesting actionable insights. Thanks to real-time network insights, it also detects suspicious devices as they speak to the network.
While testing this feature, our customers noticed that 30% of their devices weren’t tracked in their manual inventory spreadsheets. We’ve observed how a mix of human errors, high maintenance effort, and low perceived value results in outdated inventories.
We though we had 300 devices in our plant, Continuous Inventory revealed we had over 400. Now this inventory is the centerpiece of our security solution. With no effort, we have a full view of our network, and we feel confident we don’t have big security gaps.
Continuous Inventory has significantly reduced the time we spent performing manual checks on our devices that used to take hours. It’s a game changer.
[…] Other teams ping us before connecting a new device to the network, as they know we’ll quickly detect it. They feel better because they are not doing things behind our back, and we have a heads up to explore possible security implications.
CIO, Leading automotive industry company
At Safetybits, we follow OTSPM principles. With each new feature, we demonstrate that integrating all security tools supercharges threat detection and makes life easier for security engineers.
Inventory is the corner of this methodology. After all, you cannot secure what you cannot see.
Let’s see Continuous Inventory in action!
Unveiling Forgotten Devices
You can forget to register new devices in the inventory for many reasons. For example, you may be updating dumb devices that you didn’t need to manage with newer, smarter ones that do connect to the network and require firmware updates. Let’s see how Safetybits OTSPM Platform manages this scenario.
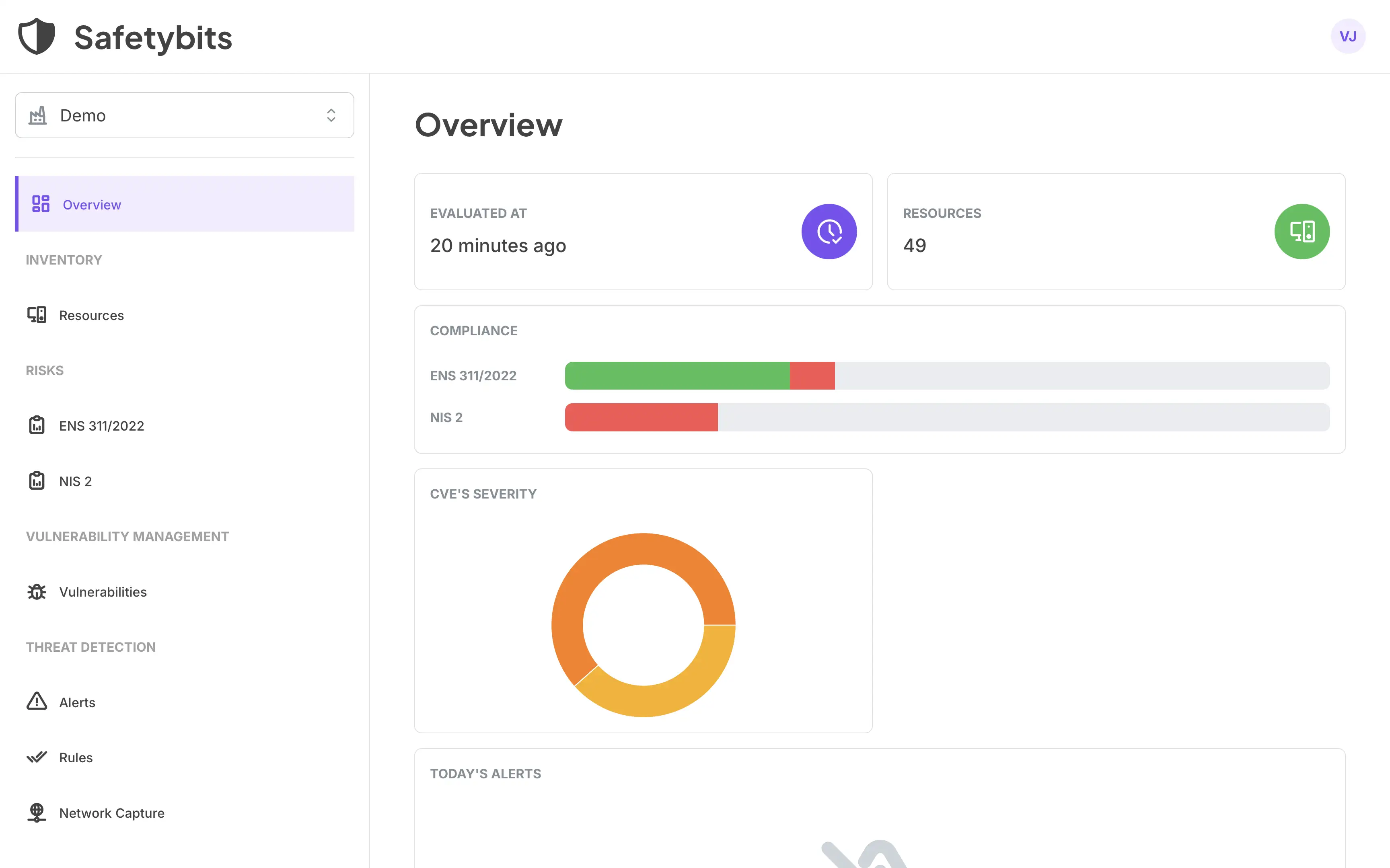
As you deploy Safetybits Agent in your infrastructure, it will start scanning the network, and you’ll see new devices popping up on the Inventory dashboard. In our case, it looked like this:
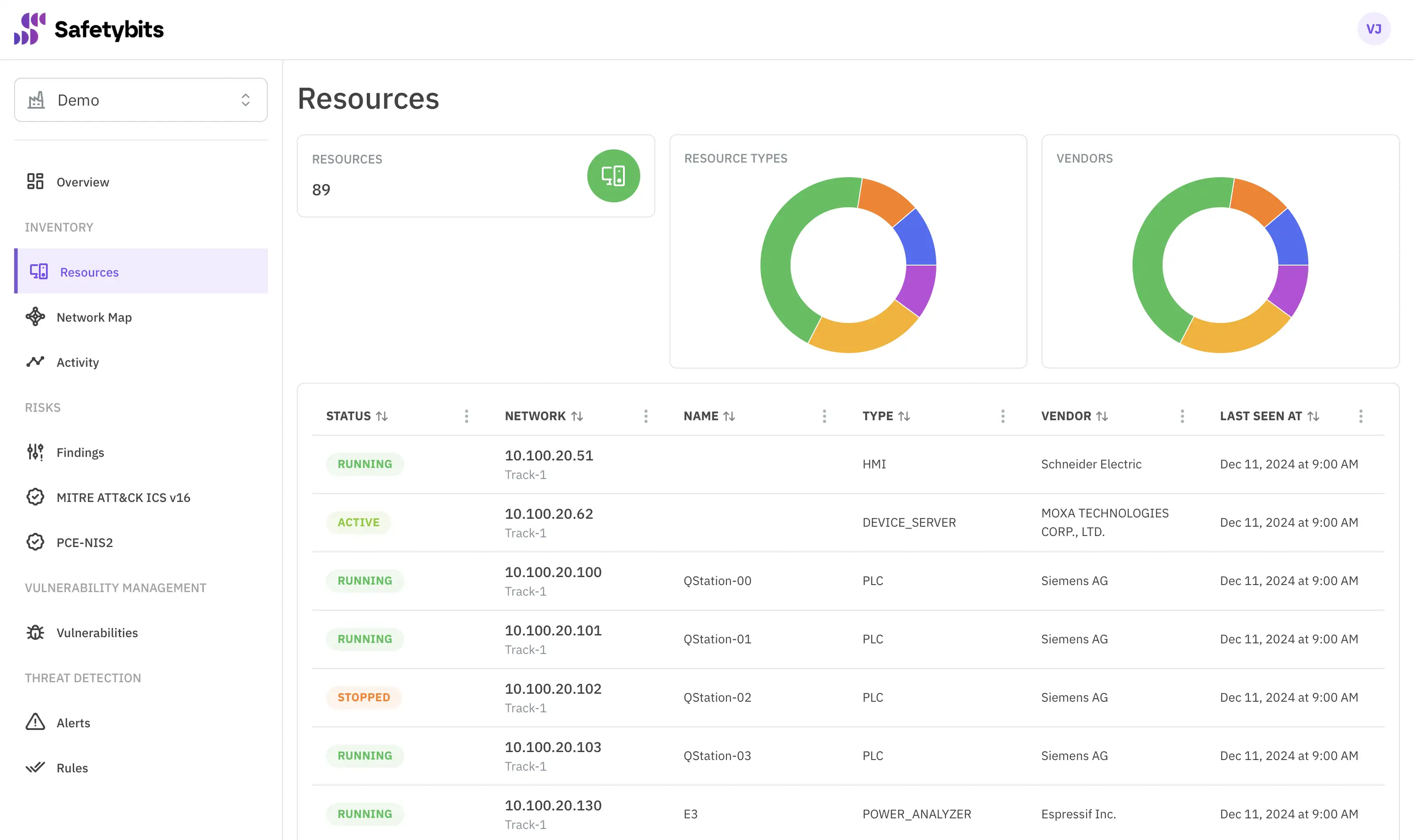
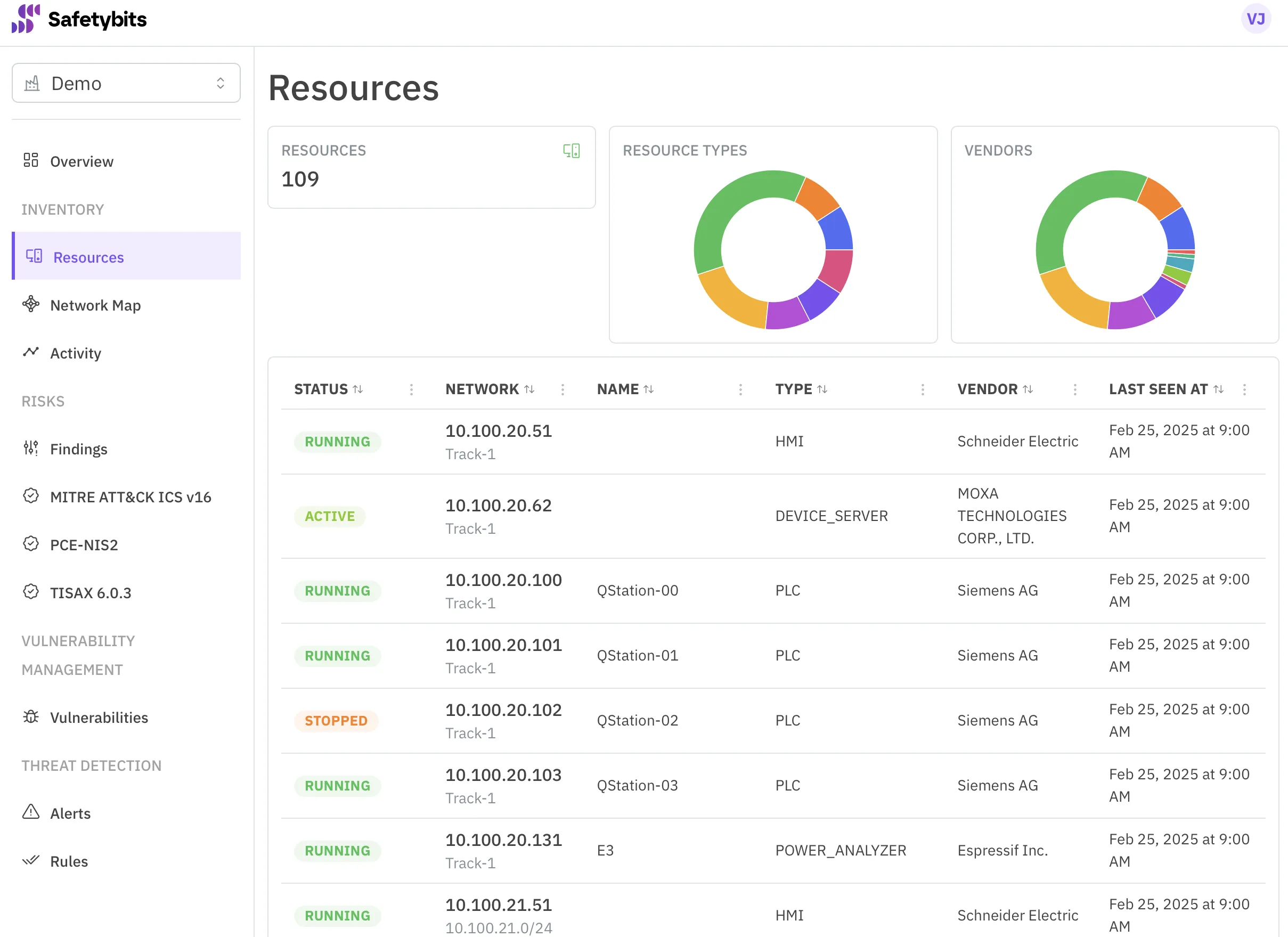
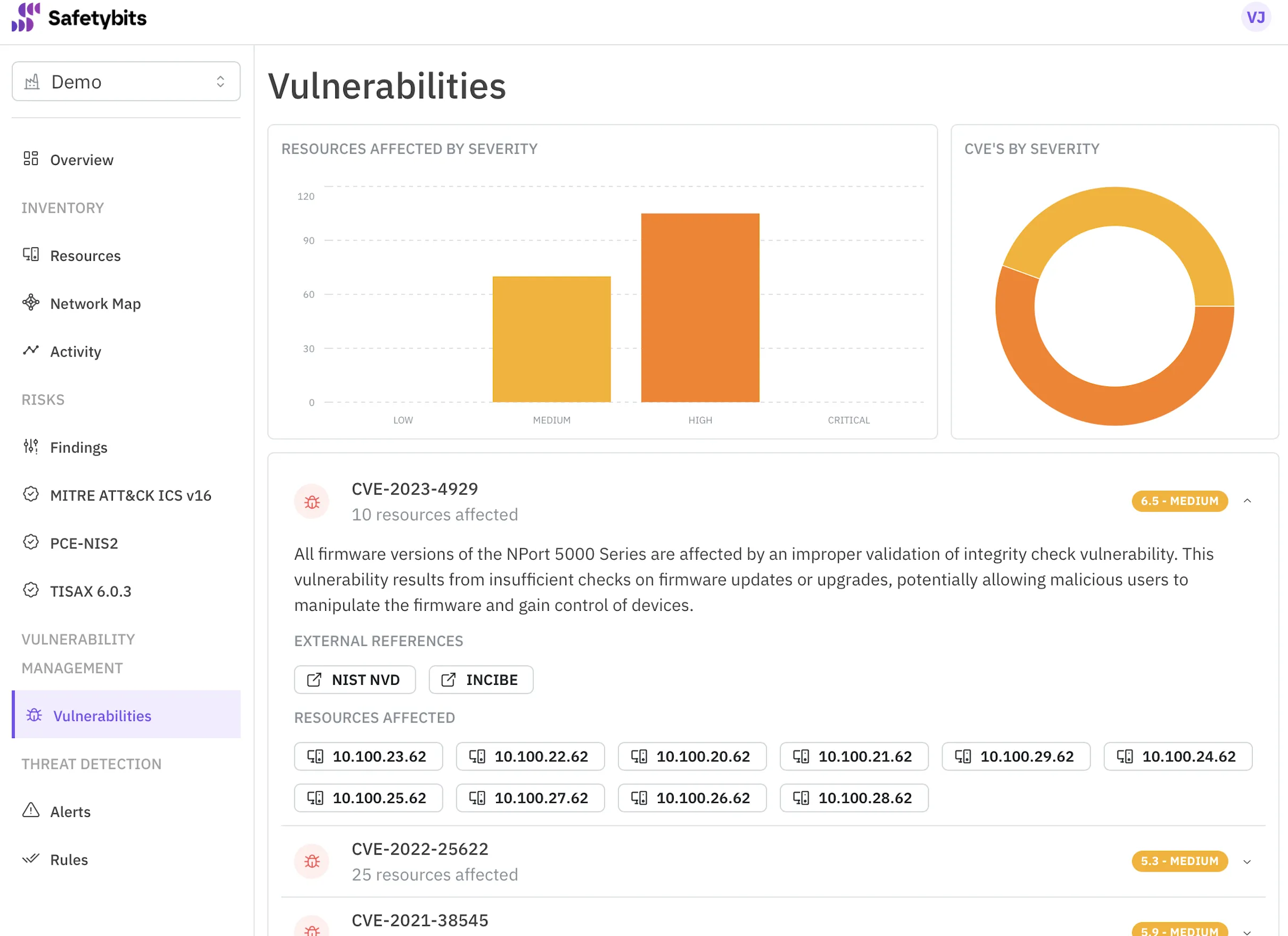
Thanks to the metadata embedded into the inventory, we could cross-reference this list with our manual inventory and discover many new devices. The filtering tool helped us navigate all this data and realize all the new devices were from the same brand.
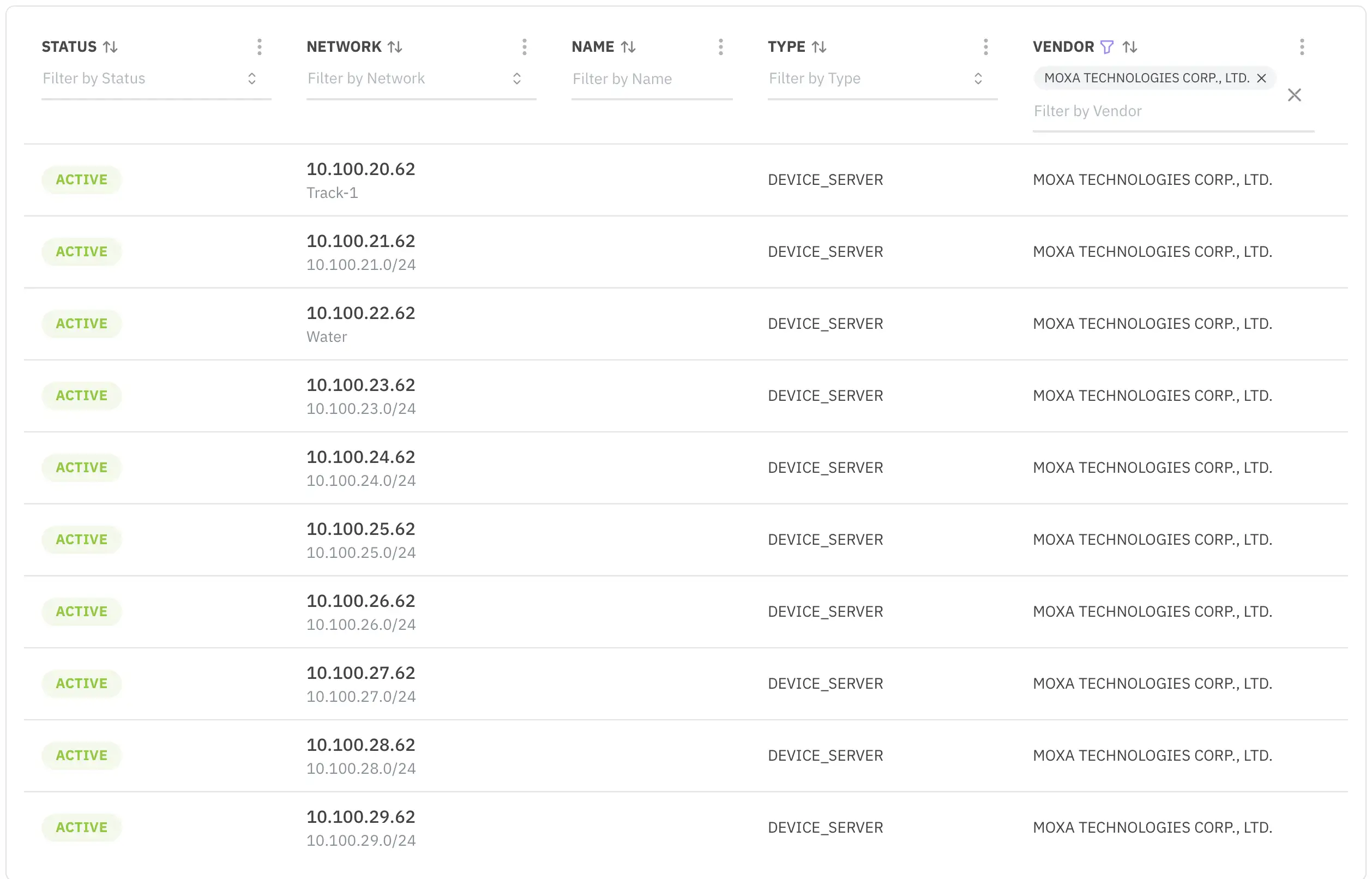
It turns out we replaced the power meters a while ago and forgot to update the inventory.
Once our inventory was scanned, it took seconds to get a list of devices needing firmware updates or that were using default credentials.
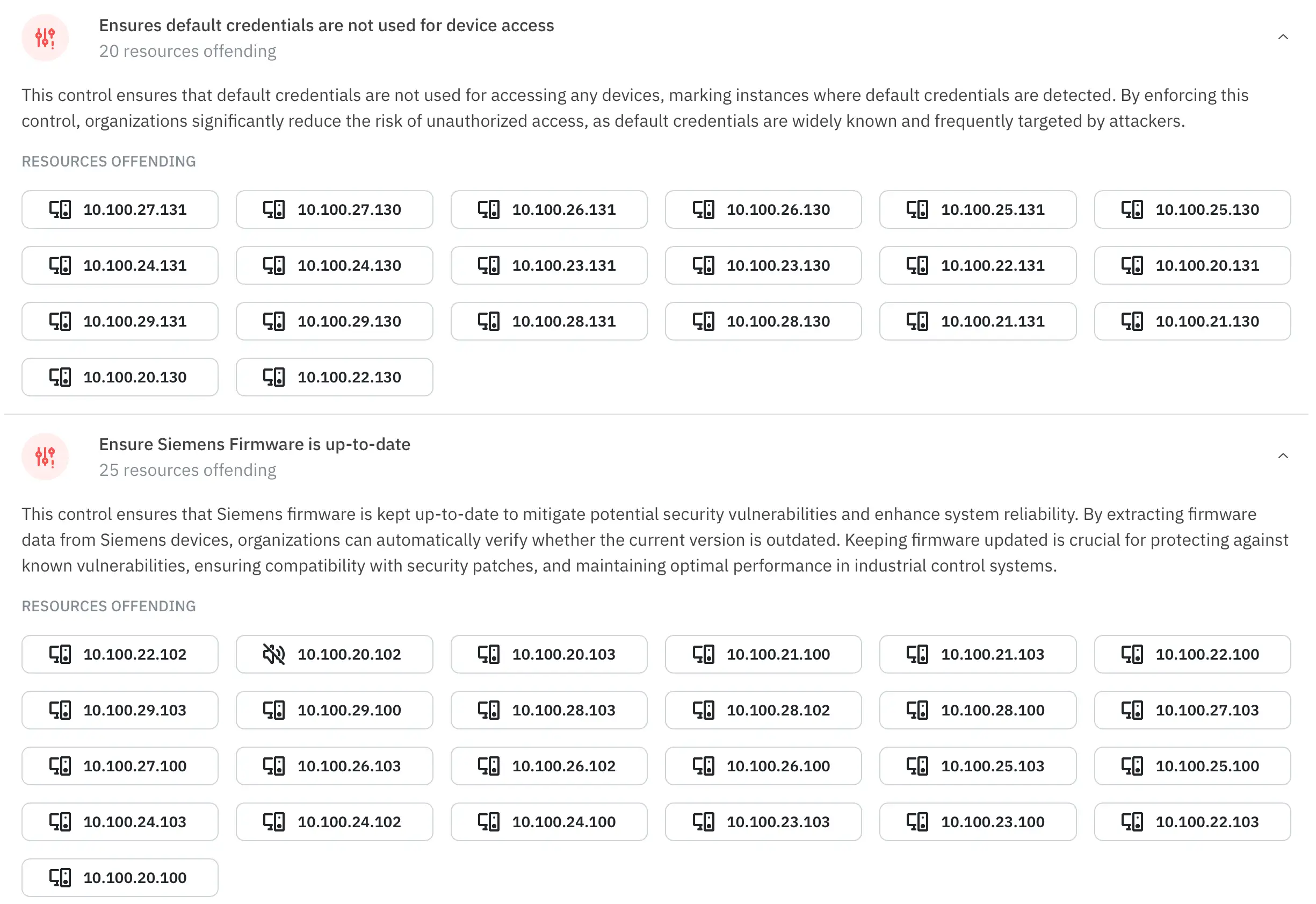
Gathering this intel before would have taken us several hours.
Investigating new Devices on the Network
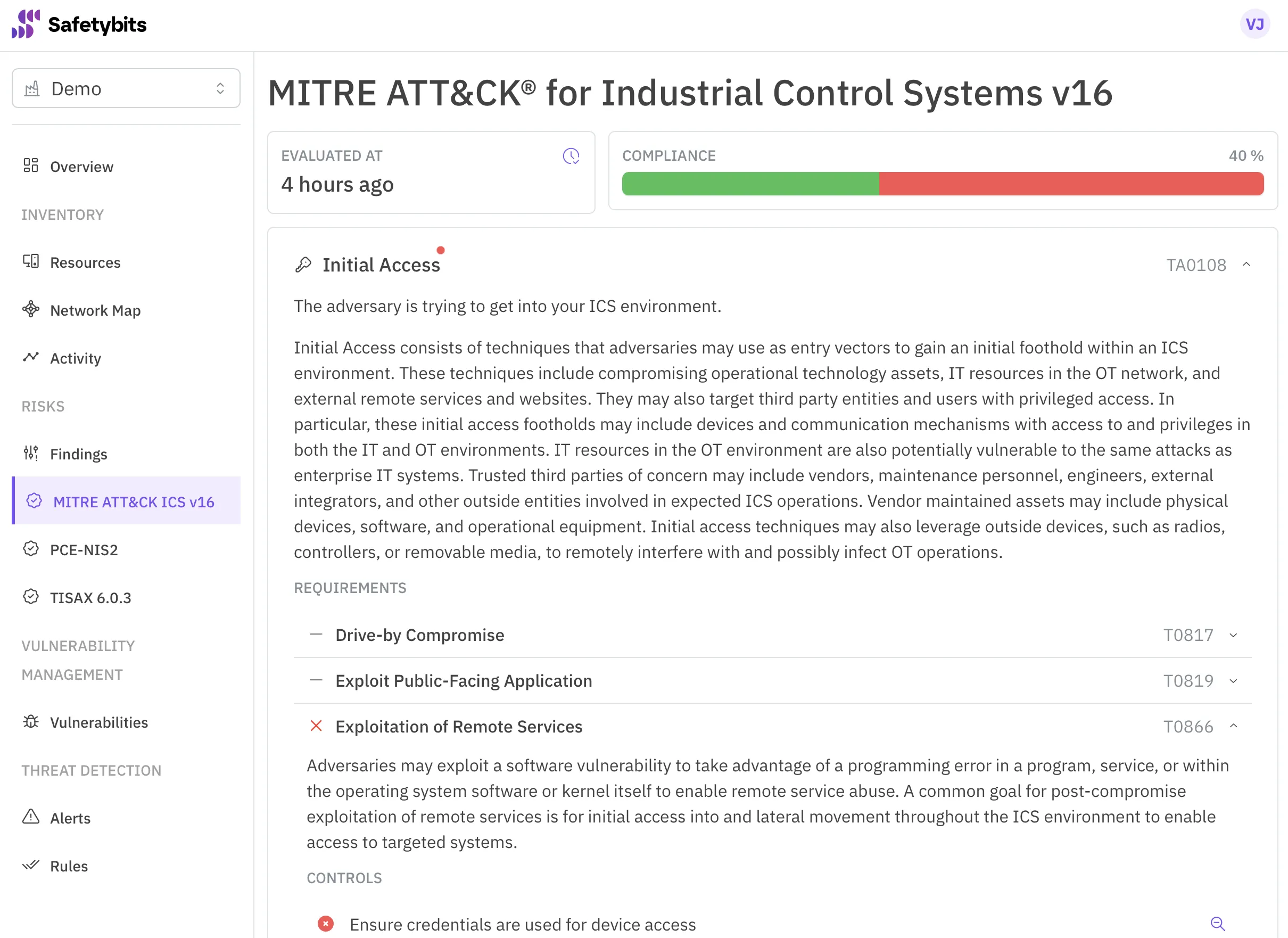
A few days have passed since we installed Continuous Inventory, and everything has worked great. It was a great help in complying with the NIS 2 European directive.
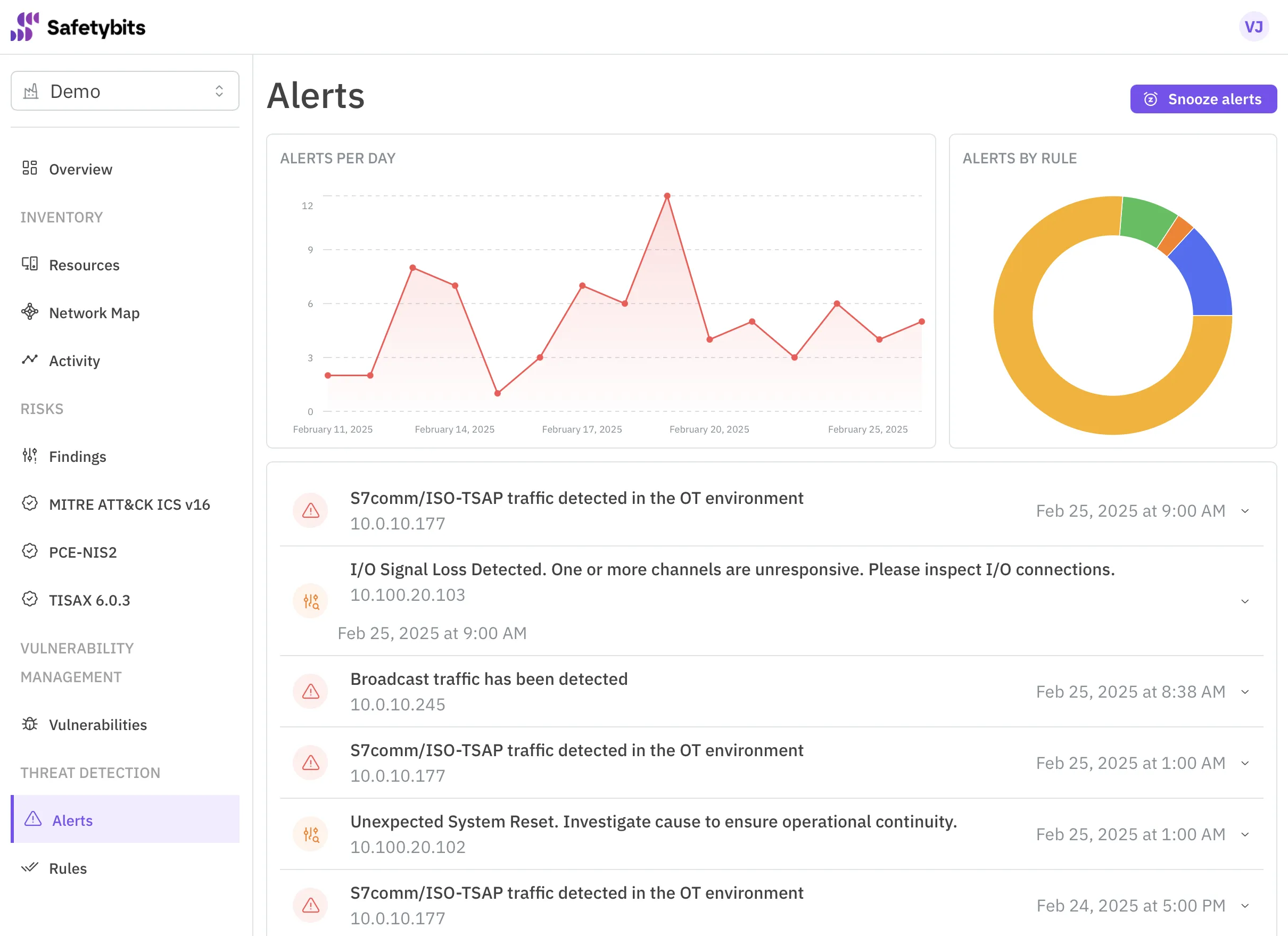
Today, when arriving at the office, we noticed two “Unrecognized Device in Network” alerts:
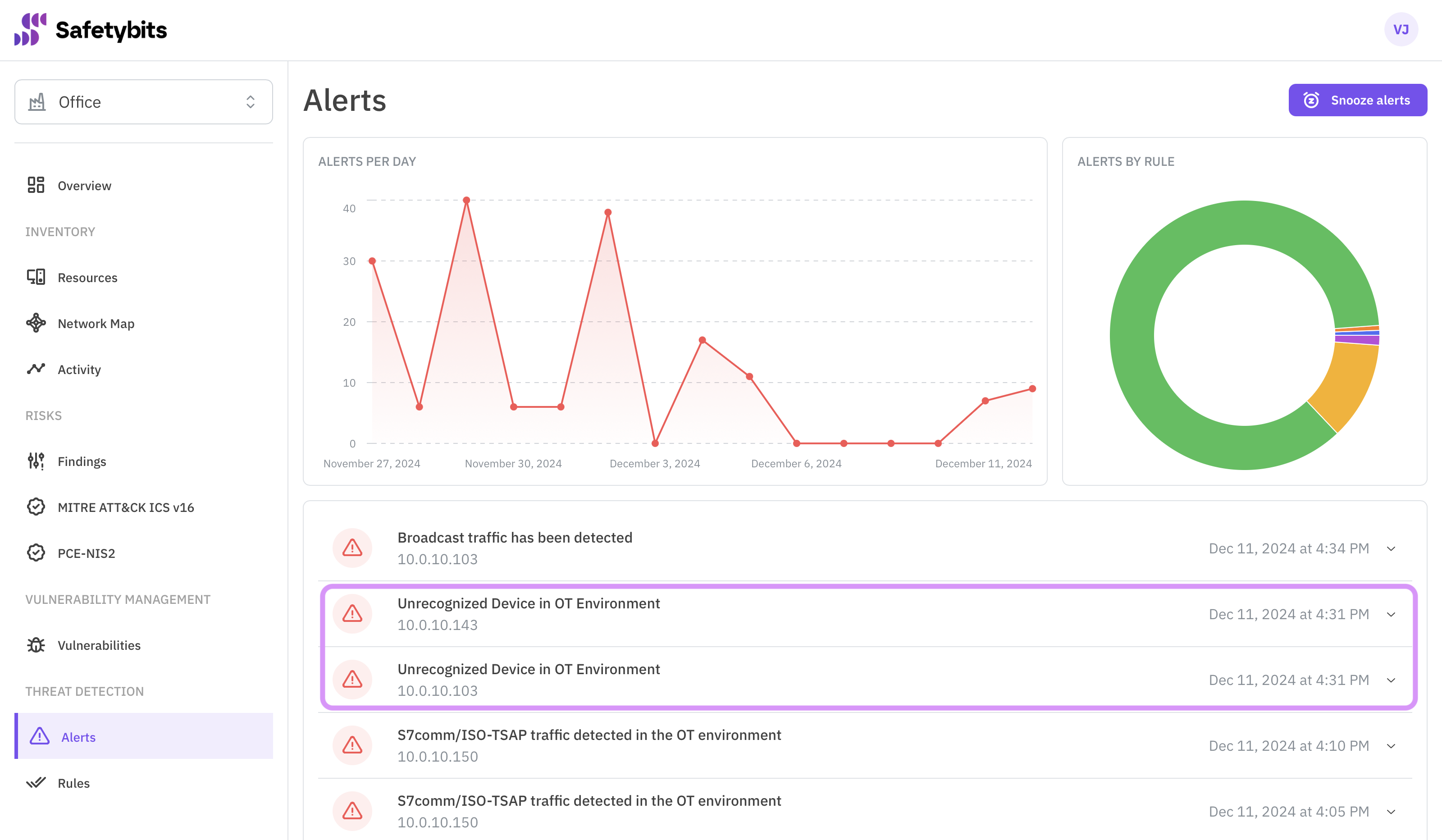
Let’s investigate the first one.
We dig into the alert details and navigate to the details of the device that originated the alert. We noticed that this device is from Prusa Research s.r.o., doesn’t have other associated alerts, and has an IP address 10.0.10.143.

After correlating the IP address with our switch configuration, we track the device to the maintenance technicians’ quarters. There we find this:
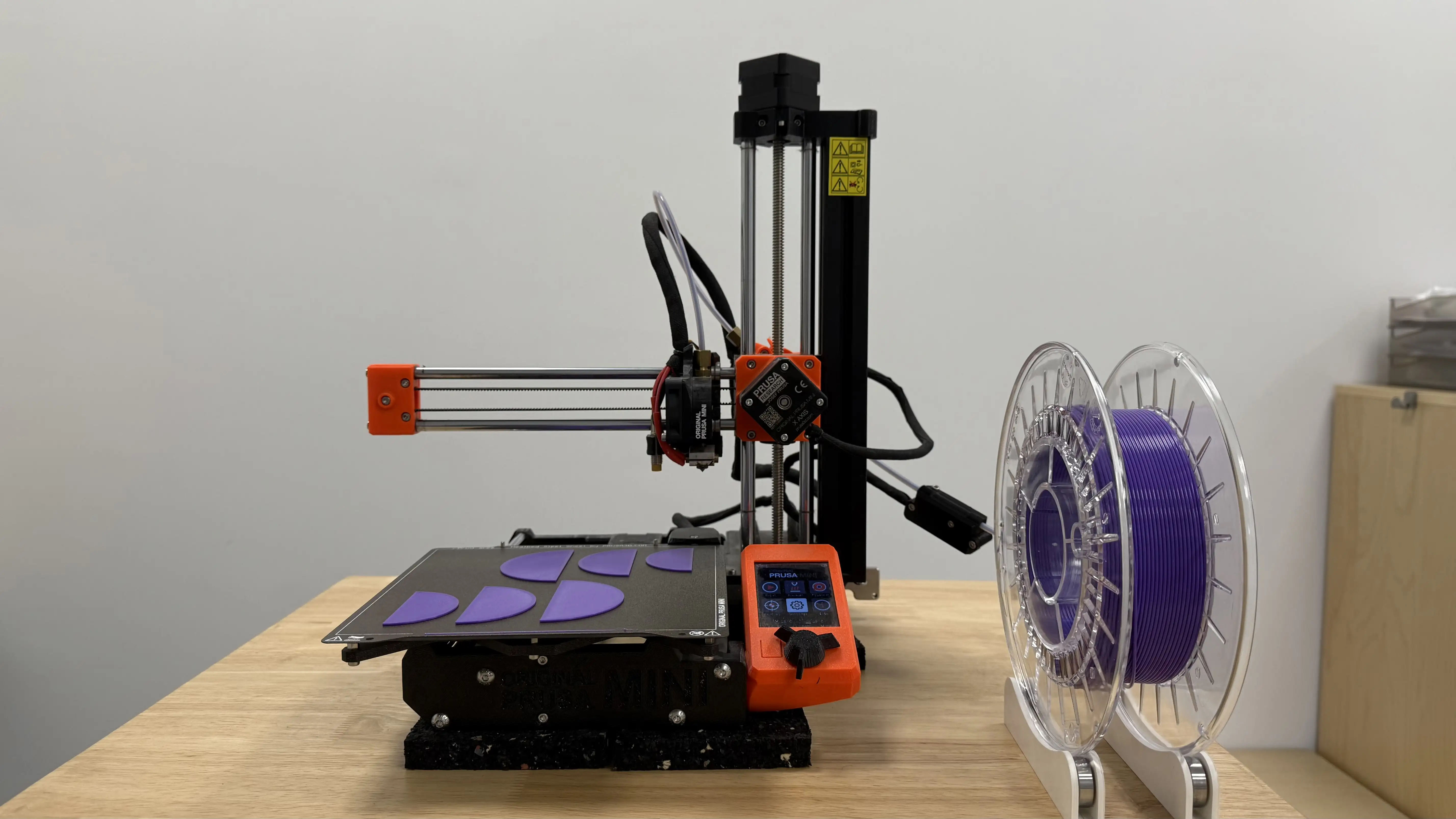
It turns out they just installed a new 3D Printer and hooked it to the network without letting us know. We don’t have any issue with the device itself, and they need it to print replacements for the machinery. It’s not a big issue; we detected the device and can now secure it.
Let’s follow the same process to investigate the other alert. In this case, we can see it is a Raspberry PI that has triggered some broadcast traffic alerts.
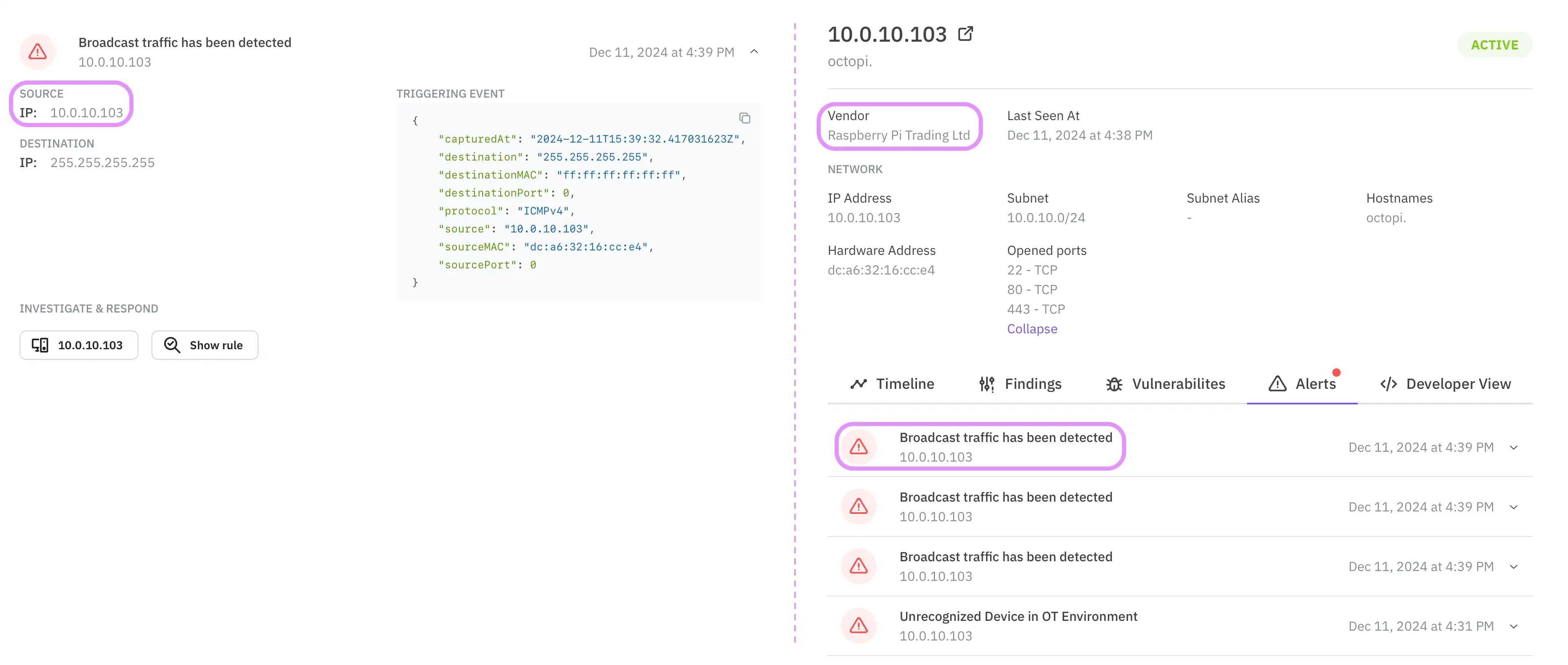
We track the IP to one cabinet on the production line. There, we find a hidden device that a casual visual inspection would have missed.

Further investigation of the device reveals it has a script to gather intel on the facility. This is definitely a malicious device, probably placed by a disgruntled employee. Time to speak with HR.
Conclusion
Safetybits Continuous Inventory turns a painful task into an enjoyable and valuable ally.
It uncovers hidden devices in your network and guides you on how to secure them and comply with security standards.
Expand your reach with OTSPM
The narrower your view, the less risks you can detect. Discover how an OTSPM platform leverages correlation to expand your reach.
Discover more →